The .AES Javascript Evil Ransomware is a new strain of the JavaScript Evil ransomware that features slight code modifications and marks all processed files with the .aes extension.
Manual Removal Guide
Recover .AES Javascript Evil Ransomware Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does .AES Javascript Evil Ransomware Infiltrate the System?
The relatively low number of captured .AES Javascript Evil Ransomware samples does not reveal the main strategy used by the criminals. We suspect that they are going to employ the most popular ones.
Email spam messages are a leading cause of infections. Typically they use social engineering tricks that confuse the targets into infecting themselves. This is done by utilizing templates (with text and graphics) that make the messages appear as being sent from a legitimate company. The .AES Javascript Evil Ransomware can either be directly attached linked or linked to a hacker-controlled site via a hyperlink. The criminals can maintain numerous download sites that may pose as official sources or portals for popular application. In the last few years spreading malware has become very popular on the BitTorrent P2P network.
Browser hijackers and other types of malware add-ons and programs can also trigger an infection. They are typically made for the most popular web browsers (Mozilla Firefox, Google Chrome, Internet Explorer, Microsoft Edge, Safari and Opera) and change important settings such as the default home page, search engine and new tabs page. The aim of the criminals is to redirect the victims to a hacker-controlled page where the .AES Javascript Evil Ransomware can be acquired from.
Other web scripts, ad networks and redirects can also lead to a .AES Javascript Evil Ransomware infection.
Related: Javascript Evil Ransomware Virus , EvilLock Ransomware
Infection Flow of .AES Javascript Evil Ransomware
.AES Javascript Evil Ransomware is a new malware strain that has just been detected by security researchers. The initial analysis shows that it is descendant from the JavaScript Evil ransomware, a virus that infected targets a few months ago.
The .Aes JavaScript Evil virus engine features only slight changes as compared to its source while at the same time following the same infection routine. After the ransomware has gained access to the victim machine the encryption process is automatically started. It seeks to process as many system and user files as possible. The affected file type extensions are encrypted according to a built-in list of file type extensions. In most cases this includes the most popular data: music, photos, videos, documents, databases, backups, configuration files and etc.
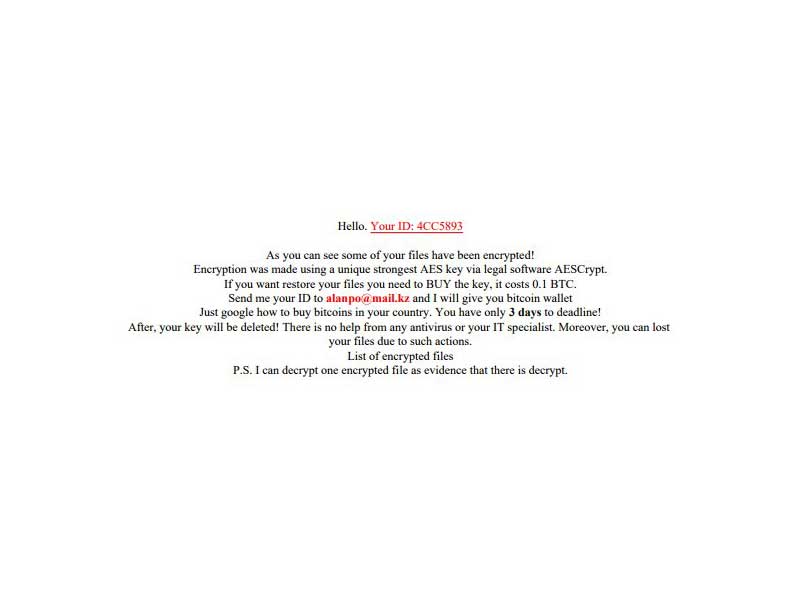
Once this part of the .AES JavaScript Evil ransomware is complete a ransomware note is crafted and shown to the victims. It reads the following message:
Hello. Your ID: 4CC5893
As you can see some of your files have been encrypted!
Encryption was made using a unique strongest AES key via legal software AESCrypt.
If you want restore your files you need to BUY the key, it costs 0.1 BTC.
Send me your ID to [email protected] and I will give you bitcoin wallet
Just google how to buy bitcoins in your country. You have only 3 days to deadline!
After, your key will be deleted! There is no help from any antivirus or your IT specialist. Moreover, you can lost
your files due to such actions.
List of encrypted files
P.S. I can decrypt one encrypted file as evidence that there is decrypt.
From this note we can conclude the following about the .AES JavaScript Evil Ransomware:
- The hackers assign a unique ID to each infected victim. In most cases this is done by extracting information about the hardware and associated software configuration during the initial infection. The ID is generated by using an algorithm using the harvested data as input parameters.
- Very limited information about the ransomware payment is provided. This leaves inexperienced victims with many questions about the nature of the issue.
- The quoted ransomware sum of 0.1 Bitcoins is about 260 US Dollars in today’s currency exchange rate.
- The hacker-provided email is hosted on a popular service that originates from Kazakhstan.
- The criminals impose a time limit upon the victims to further pressure them into paying the ransomware sum.
Using a quality anti-spyware solution guarantees the efficient removal of the infections. Using a professional-grade data recovery software the affected files can be recovered. Refer to our guide below for in-depth instructions.
Remove .AES Javascript Evil Ransomware and Restore Data
WARNING! Manual removal of .AES Javascript Evil Ransomware requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
.AES Javascript Evil Ransomware – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
.AES Javascript Evil Ransomware Files
WARNING! All files and objects associated with .AES Javascript Evil Ransomware should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD .AES Javascript Evil Ransomware Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



