A security expert from AVG has discovered a ransomware called Fantom that is based on the EDA2 open source code and poses as a fake Microsoft Windows update. No decryptor is available for this malware is available yet.
The Fantom Ransomware Poses as a Windows Update
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Jakub Kroustek, a security expert from AVG, has discovered the Fantom ransomware which is based on the EDA2 open source code. The developers have disguised the threat as a critical update for the Microsoft Windows operating systems by cloning some of the meta data that is embedded in the executable file.
Upon execution the ransomware spawns an embedded file called WindowsUpdate.exe which shows the Windows update screen. This window is displayed as an overlay that restricts interaction with all other open programs. The counterfeit counter shows a percentage timer that increases as the ransomware encrypts the user data in the background. The unsuspecting user is fooled into believing that a legitimate update is in process, but in truth his/her files are being compromised. If the user closes the screen by applying the keyboard shortcut CTRL + F4 the overlay disappears, however the ransomware continues to run in the background. Upon successful execution Fantom also creates two batch files that delete the Windows Volume Copies and the counterfeit Windows update file.
Fantom uses the AES-128 cipher with the RSA public-private key method to encrypt the victim files. It works alongside with a malicious remote C&C server where the generated private key is stored. The ransomware creates a ransom note “DECRYPT_YOUR_FILES.HTML” in each folder where files are affected.
The final phase of infection is the download of an image that is saved into the %UserProfile%\2d5s8g4ed.jpg location.
Further Information
The following files are created by the malware executable:
- %AppData%\delback.bat
- [Executable_Path]\WindowsUpdate.exe
- [Executable_Path]\update.bat
- %UserProfile%\2d5s8g4ed.jpg
- HKCU\Control Panel\Desktop\ “Wallpaper” “%UserProfile%\How to decrypt your files.jpg”
- HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableTaskMgr” = 1
- http://powertoolsforyou.com/themes/prestashop/cache/stats.php
- http://templatesupdates.dlinkddns.com/falssk/fksgieksi.php
The following registry entries are added:
Network communication is carried to the following hosts:
Affected file extensions include:
.001, .1cd, .3d, .3d4, .3df8, .3fr, .3g2, .3gp, .3gp2, .3mm, .7z, .aac, .abk, .abw, .ac3, .accdb, .ace, .act, .ade, .adi, .adpb, .adr, .adt, .ai, .aim, .aip, .ais, .amf, .amr, .amu, .amx, .amxx, .ans, .ap, .ape, .api, .apk, .arc, .arch00, .ari, .arj, .aro, .arr, .arw, .asa, .asc, .ascx, .ase, .asf, .ashx, .asmx, .asp, .aspx, .asr, .asset, .avi, .avs, .bak, .bar, .bay, .bc6, .bc7, .bck, .bdp, .bdr, .bib, .bic, .big, .bik, .bkf, .bkp, .blob, .blp, .bmc, .bmf, .bml, .bmp, .boc, .bp2, .bp3, .bpl, .bsa, .bsp, .cag, .cam, .cap, .car, .cas, .cbr, .cbz, .cc, .ccd, .cch, .cd, .cdr, .cer, .cfg, .cfr, .cgf, .chk, .clr, .cms, .cod, .col, .cp, .cpp, .cr2, .crd, .crt, .crw, .cs, .csi, .cso, .css, .csv, .ctt, .cty, .cwf, .d3dbsp, .dal, .dap, .das, .dayzprofile, .dazip, .db0, .dbb, .dbf, .dbfv, .dbx, .dcp, .dcr, .dcu, .ddc, .ddcx, .dem, .der, .desc, .dev, .dex, .dic, .dif, .dii, .dir, .disk, .divx, .diz, .djvu, .dmg, .dmp, .dng, .dob, .doc, .docm, .docx, .dot, .dotm, .dotx, .dox, .dpk, .dpl, .dpr, .dsk, .dsp, .dvd, .dvi, .dvx, .dwg, .dxe, .dxf, .dxg, .elf, .epk, .eps, .eql, .erf, .err, .esm, .euc, .evo, .ex, .exif , .f90, .faq, .fcd, .fdr, .fds, .ff, .fla, .flac, .flp, .flv, .for, .forge, .fos, .fpk, .fpp, .fsh, .gam, .gdb, .gho, .gif, .grf, .gthr, .gz, .gzig, .gzip, .h3m, .h4r, .hkdb, .hkx, .hplg, .htm, .html, .hvpl, .ibank, .icxs, .idx, .ifo, .img, .indd, .ink, .ipa, .isu, .isz, .itdb, .itl, .itm, .iwd, .iwi, .jar, .jav, .java, .jc, .jfif, .jgz, .jif, .jiff, .jpc, .jpe, .jpeg, .jpf, .jpg, .jpw, .js, .json, .kdb, .kdc, .kf, .kmz, .kwd, .kwm, .layout, .lbf, .lbi, .lcd, .lcf, .ldb, .lgp, .litemod, .log, .lp2, .lrf, .ltm, .ltr, .ltx, .lvl, .m2, .m2v, .m3u, .m4a, .mag, .man, .map, .max, .mbox, .mbx, .mcd, .mcgame, .mcmeta, .md, .md3, .mdb, .mdbackup, .mddata, .mdf, .mdl, .mdn, .mds, .mef, .menu, .mic, .mip, .mkv, .mlx, .mod, .mov, .moz, .mp3, .mp4, .mpeg, .mpg, .mpqge, .mrw, .mrwref, .msg, .msp, .mxp, .nav, .ncd, .ncf, .nds, .nef, .nfo, .now, .nrg, .nri, .nrw, .ntl, .odb, .odc, .odf, .odi, .odm, .odp, .ods, .odt, .odtb .oft, .oga, .ogg, .opf, .orf, .owl, .oxt, .p12, .p7b, .p7c, .pab, .pak, .pbf, .pbp, .pbs, .pcv, .pdd, .pdf, .pef, .pem, .pfx, .php, .pkb, .pkh, .pkpass, .pl, .plc, .pli, .pm, .png, .pot, .potm, .potx, .ppd, .ppf, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prc, .prt, .psa, .psd, .psk, .pst, .ptx, .puz, .pwf, .pwi, .pwm, .pxp, .py, .qbb, .qdf, .qel, .qic, .qif, .qpx, .qtq, .qtr, .r3d, .ra, .raf, .rar, .raw, .rb, .re4, .res, .rev, .rgn, .rgss3a, .rim, .rng, .rofl, .rrt, .rsrc, .rsw, .rte, .rtf, .rts, .rtx, .rum, .run, .rv, .rw2, .rwl, .sad, .saf, .sav, .sb, .sc2save, .scm, .scn, .scx, .sdb, .sdc, .sdn, .sds, .sdt, .sen, .sfs, .sfx, .sh, .shar, .shr, .shw, .sid, .sidd, .sidn, .sie, .sis, .slm, .sln, .slt, .snp, .snx, .so, .spr, .sql, .sqx, .sr2, .srf, .srt, .srw, .ssa, .std, .stt, .stx, .sud, .sum, .svg, .svi, .svr, .swd, .swf, .syncdb, .t12, .t13, .tar, .tax, .tax2015, .tax2016, .tbz2, .tch, .tcx, .text, .tg, .thmx, .tif, .tlz, .tor, .tpu, .tpx, .trp, .tu, .tur, .txd, .txf, .txt, .uax, .udf, .umx, .unity3d, .unr, .unx, .uop, .upk, .upoi, .url, .usa, .usx, .ut2, .ut3, .utc, .utx, .uvx, .uxx, .val, .vc, .vcd, .vdf, .vdo, .ver, .vfs0, .vhd, .vmf, .vmt, .vob, .vpk, .vpp_pc, .vsi, .vtf, .w3g, .w3x, .wad, .war, .wav, .wave, .waw, .wb2, .wbk, .wdgt, .wks, .wm, .wma, .wmd, .wmdb, .wmmp, .wmo, .wmv, .wmx, .wotreplay, .wow, .wpd, .wpk, .wpl, .wps, .wsh, .wtd, .wtf, .wvx, .x3f, .xf, .xl, .xla, .xlam, .xlc, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xltx, .xlv, .xlwx, .xml, .xpi, .xpt, .xvid, .xwd, .xxx, .yab, .yps, .z02, .z04, .zap, .zip, .zipx, .zoo, .ztmp
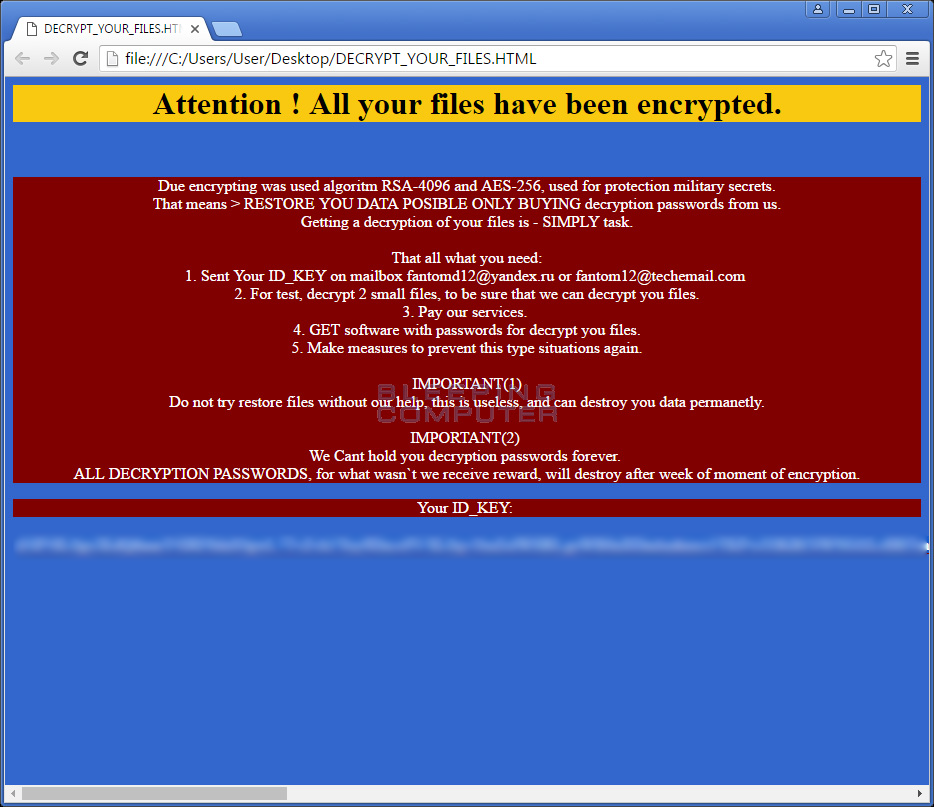
New Fantom Ransomware Strain released
Security researchers have identified a new Fantom ransomware strain which uses the [email protected] contact email.
The compromised files receive the .locked4 extension and the ransomware note is crafted following the RESTORE-FILES!
You can remove it by using a trusted anti-spyware tool.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



