Malware researchers just discovered a new threat known as the Jaff ransomware virus. It is currently being analyzed however the initial analysis shows that it encrypts user data, appends the .jaff file extension to the marked files and extorts the victims for a ransomware fee. You can remove JAFF ransomware virus via:
DOWNLOAD JAFF Virus Removal Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Once the Jaff ransomware virus is removed successfully, you can try to restore your files following our instructions below.
The Jaff Ransomware Virus Impact on an Infected PC
Security researchers uncovered a ransomware virus which is currently being under analysis. The threat is called Jaff ransomware virus and it’s created by an unknown hacker. Right now the initial data does not show a correlation between the captured samples and the most popular malware families. Upon infection the Jaff ransomware virus follows a predefined behavior patterns that is typical for this type of malware.
One of the first actions is the environment check. This includes both system information harvesting and other environment analysis. The main Jaff ransomware virus module identifies if the infected host is a virtual machine, debugging environment or a sandbox environment. If such fingerprints are identified the infection is immediately halted. This is done to prevent the system administrators from discovering the infection. In addition, the engine may also disable or delete any running or installed anti-virus software solutions to prevent automated removal.
Similar Viruses: CryptConsole ransomware, Sardoninir ransomware, EnCrYpTeD ransomware
When this is done the Jaff virus engine automatically gathers information such as: the active computer name, the unique cryptographic machine GUID, system registry and browser data. An unusual tactic employed by its creators is the fact that the Jaff ransomware virus features behavior that is very similar to the actions performed by browser hijackers. The malware is able to extract settings and stored data from popular web browsers (Microsoft Edge, Internet Explorer, Google Chrome and Mozilla Firefox) such as: stored cookies, account credentials, bookmarks, form data and etc. The security analysis shows that the virus code can modify proxy and sensitive Internet Explorer settings. They can be used to institute additional malware to the computers. Proxy changes can relay all generated network traffic through hacker-controlled servers. This can be used to eavesdrop on all communications and allow the criminal to execute dangerous man-in-the-middle attacks.
The extracted data is also used to calculate the unique machine infection ID. Another characteristic that is attributed to the malware is that it gains privileges to delete important system and user files. Using the proper configuration this allows the hackers to completely sabotage the victim computers.
The Jaff ransomware virus creates an persistent environment. This means that it actively monitors key registry entries for modification and prevents any manual removal methods. Effectively the only way to restore the computers and the affected data is to use a quality anti-malware solution and data recovery products. You can read more in our removal and recovery section below.
When these processes are complete the encryption commands are started. The following file type extensions are processed by it:
.xlsx, .acd, .pdf, .pfx, .crt, .der, .cad, .dwg, .MPEG, .rar, .veg, .zip, .txt, .jpg, .doc, .wbk, .mdb, .vcf, .docx, .ics, .vsc, .mdf, .dsr, .mdi, .msg, .xls, .ppt, .pps, .obd, .mpd, .dot, .xlt, .pot, .obt, .htm, .html, .mix, .pub, .vsd, .png, .ico, .rtf, .odt, .3dm, .3ds, .dxf, .max, .obj, .7z, .cbr, .deb, .gz, .rpm, .sitx, .tar, .tar.gz, .zipx, .aif, .iff, .m3u, .m4a, .mid, .key, .vib, .stl, .psd, .ova, .xmod, .wda, .prn, .zpf, .swm, .xml, .xlsm, .par, .tib, .waw, .001, .002, 003., .004, .005, .006, .007, .008, .009, .010, .contact, .dbx, .jnt, .mapimail, .oab, .ods, .ppsm, .pptm, .prf, .pst, .wab, .1cd, .3g2, .7zIP, .accdb, .aoi, .asf, .asp., aspx, .asx, .avi, .bak, .cer, .cfg, .class, .config, .css, .csv, .db, .dds, .fif, .flv, .idx, .js, .kwm, .laccdb, .idf, .lit, .mbx, .md, .mlb, .mov, .mp3, .mp4, .mpg, .pages, .php, .pwm, .rm, .safe, .sav, .save, .sql, .srt, .swf, .thm, .vob, .wav, .wma, .wmv, .xlsb, .aac, .ai, .arw, .c, .cdr, .cls, .cpi, .cpp, .cs, .db3, .docm, .dotm, .dotx, .drw, .dxb, .eps, .fla, .flac, .fxg, .Java, .m, .mov, .pcd, .pct, .pl, .potm, .potx, .ppam, ppsx, .ps, .pspimage, .r3d, .rw2, .sldm, .sldx, .svg, .tga, .wps, .xla, .xlam, .xlm, .xltm, .xltx, .x1w, .act, .adp, .al, .bkp, .blend, .cdf, .cdx, .cgm, .cr2, .dac, .dbf, .dcr, .ddd, .design, .dtd, .fdb, .fff, .fpx, .h, .iif, .indd, .jpeg, .mos, .nd, .nsd, .nsf, .nsg, .nsh, .odc, .odp, .oil, .pas, .pat, .pef, .ptx, .qbb, .qbm, .sas7bdat, .say, .st4, .st6, .stc, .sxc, .sxw, .tlg, .wad, .xlk, .aiff, .bin, .bmp, .cmt, .dat, .dit, .edb, .flvv, .gif, .groups, .hdd, .hpp, .log, .m2ts, .m4p, .mkv, .ndf, .nvram, .ogg, .ost, .pab, .pdb, .pif, .qed, .qcow, .qcow2, .rvt, .st7, .stm, .vbox, .vdi, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .3fr, .3pr, .ab4, .accde, .accdt, .ach, .acr, .adb, .srw, .st5, .st8, .std, .sti, .stw, .stx, .sxd, .sxg, .sxi, .sxm, .tex, .wallet, .wb2, .wpd, .x11, .x3f, .xis, .ycbcra, .qbw, .qbx, .qby, .raf, .rat, .raw, .rdb, rwl, .rwz, .s3db, .sdO, .sda, .sdf, .sqlite, .sqlite3, .sqlitedb, .sr, .srf, .oth, .otp, .ots, .ott, .p12, .p7b, .plc, .pdd, .pem, .plus_muhd, .plc, .pptx, .psafe3, .py, .qba, .qbr.myd, .ndd, .nef, .nk, .nop, .nrw, .nsg, .ns3, .ns4, .nwb, .nx2, .nxl, .nyf, .odb, .odf, .odg, .odm, .ord, .otg, .ibz, .iiq, .incpas, .jpe, .kc2, .kdbx, .kdc, .kpdx, .lua, .mdc, .mef, .mfw, .mmw, .mny, .moneywell, .mrw.des, .dgc, .djvu, .dng, .drf, .dxg, .eml, .erbsql, .erd, .exf, .ffd, .fh, .fhd, .gray, .grey, .gry, .hbk, .ibank, .cdr4, .cdr5, .cdr6, .cdrw, .ce1, .ce2, .cib, .craw, .crw, .csh, .csl, .db_journal, .dc2, .dcs, .ddoc, .ddrw, .ads, .agdl, .ait, .apj, .asm, .awg, .back, .backup, .backupdb, .bank, .bay, .bdb, .bgt, .bik, .bpw, .cdr3, .as4
The encryption engine marks the affected data with the .jaff file extension. A ransomware note is crafted once the Jaff ransomware virus has completed processing. It displays the following content:
jaff decryptor system
Files are encrypted!
To decrypt flies you need to obtain the private key.
The only copy of the private key, which will allow you to decrypt your files, is located on a secret server
in the InternetYou must install Tor Browser: https://www.torproject.org/download/download-easy.html.en
After instalation,run the Tor Browser and enter address: http://rktazuzi7hbln7sy.onion/
Follow the instruction on the web-site.
Like other similar malware the Jaff ransomware virus directs the victims to a site located on the TOR anonymous network. When they open it up the victims are greeted with a login gateway which asks them to enter the unique infection ID.
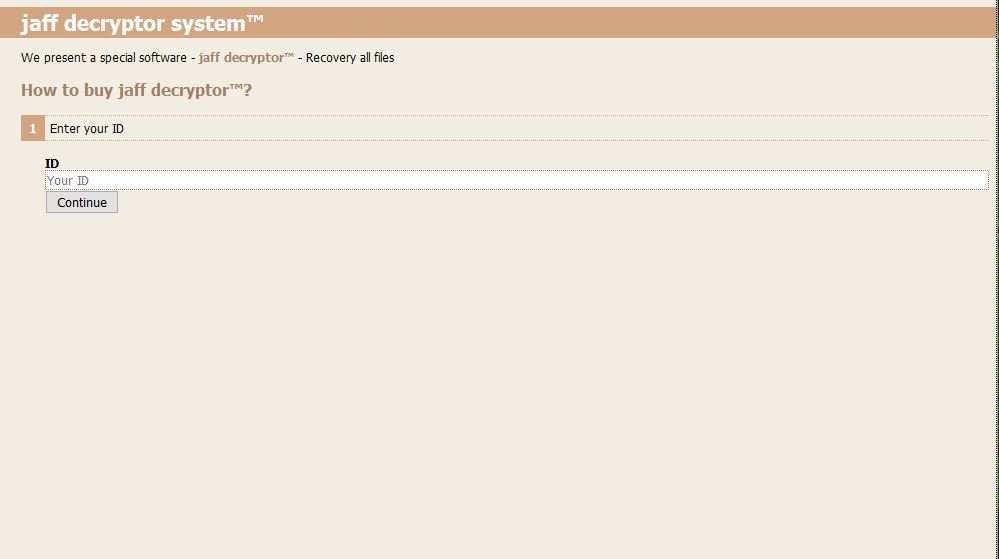
The hackers behind the virus can use various tricks and tactics to force the victims into them a ransomware fee. Some of the commonly used scenarios include the following:
- Time Limit – The hackers can institute a short time limit after which the ransomware private decryption key is destroyed or the sum is raised double.
- Trial Decryption – Sometimes the criminals behind the computer viruses attempt to win the trust of the victims by offering “free” decryption to a limited extent.
- Identity Theft – The victims are extorted of identity theft and sensitive data abuse if the money is not sent to the criminal operators.
- Varying Fee – The ransomware operators can change the amount of the ransomware fee depending on the nature of the affected data.
Jaff Ransomware Virus Distribution Methods
The current attack wave that carries the Jaff ransomware virus samples uses email spam. We suspect that the source is a large botnet or several attack servers that have been configured to spread the infections. The operators send out message with subjects that feature a keyword followed by a randomly-generated numeric ID. Examples include the following sample file names: FILE_5948340, PDF_301486, SCAN_9709455, Document_6646710, COPY_7966074. These attachments contain no body text and feature a PDF attachment named nm.pdf. It is an embedded Word .docm document that features malicious macros that serve as the payload dropper. The ongoing attack campaigns seems to focus mainly on small and medium size businesses.
The analysis made on the sent emails has shown that the hackers use a variety of compromised names and domains. The mail indicates that the criminals use randomly generated sets of first and last names that are applied to the domains. Examples include some of the following:
- Alfonzo
- Lorna
- Rigoberto
- Vera
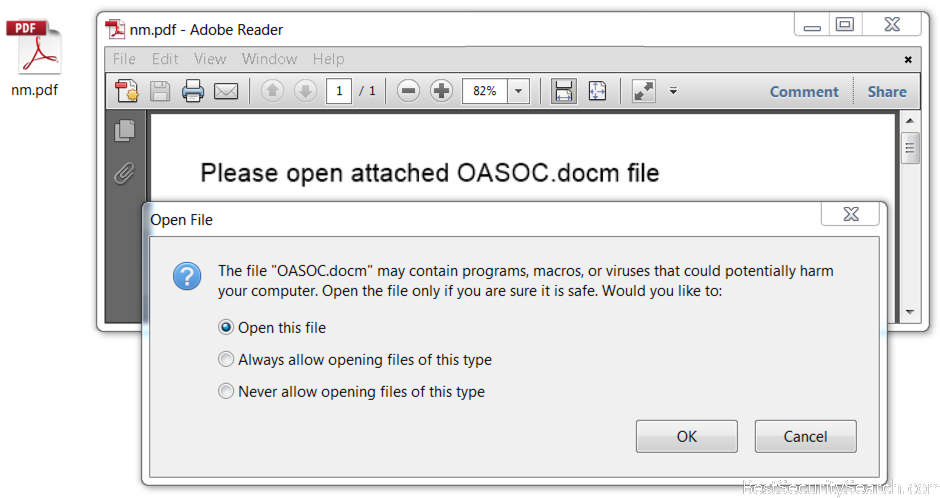 potentially harm your computer. Open the file only if you are sure it is safe. Would you like to:
potentially harm your computer. Open the file only if you are sure it is safe. Would you like to:
* Open this file
* Always allow opening files of this type
* Never allow opening files of this type
Email spam campaigns can utilize various tactics including social engineering. The hackers can attach content that appears to be incoming from legitimate users, companies or government institutions. As such the Jaff ransomware virus can be attached directly or linked in the body content. We suspect that the hackers can shift to these infection methods if the infected documents strategy does not give a high infection ratio.
Other ways of getting infected with the Jaff ransomware virus include the use of modified software installers. They are usually legitimate copies that have been modified to include the malicious code. The hackers then distribute the executable files on compromised or fake download sites and P2P networks such as BitTorrent.
The malware can also be delivered by browser hijackers. They are malicious extensions made for the most popular web browsers: Mozilla Firefox, Safari, Google Chrome, Microsoft Edge and Internet Explorer. Upon infection they modify important setting such as the default home page, default new tabs page and default search engine. In addition it harvest sensitive such as any stored account credentials, cookies, passwords, bookmarks, settings and etc.
Hacker-controlled ad networks and related redirects can also lead to a Jaff ransomware virus infection. The ad networks that are operated by the computer criminals both distribute the samples and also generate income if the users interact with them.
Another possible way of delivering the Jaff ransomware virus is by launching direct hacker intrusion attacks. The criminals use automated vulnerability testing frameworks against outdated software running on the victim computers. Security experts recommend all users to always patch their applications to the latest available versions.
Remove Jaff Ransomware Virus and Restore Jaff Encrypted Files
WARNING! Manual removal of the Jaff ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Jaff Virus – Manual Removal Steps
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
- 1) Open My Computer/This PC
2) Windows 7
- – Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
- – Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
- 1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Jaff Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
- 2) Use professional data recovery software
- – Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
- – Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
STEP VII: Preventive Security Measures
- 1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



