LOCKER-PAY Virus is a dangerous ransomware that locks the infected computer, read our removal guide to learn more about it.
Manual Removal Guide
Recover LOCKER-PAY Virus Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does LOCKER-PAY Virus Infiltrate the System?
The LOCKER-PAY virus is being distributed using different methods depending on the predefined targets. The hackers behind the infection attacks use mainly email messages. There are several different kinds that computer users can come in contact:
- Malicious File Attachments ‒ These types of messages contain body text that attempt to make the users infect themselves by downloading and executing the attached files.
- Malicious Links ‒ The emails contain malicious links that lead to virus instances.
- Hybrid Messages ‒ Such messages combine the methods above.
Malicious spam message examples include the following:
Dear Customer
We have attempted to deliver your package
The delivery attempt failed because nobody was present at the shipping
address, so this notification has been automatically sent.
You may arrange re-delivery by visiting the nearest DHL office with the
printed shipping invoice mentioned below.If the package is not scheduled for delivery or picked up within 96 hours,
it will be returned to the sender.TRACKING Number: 97 93745 186
Expected Deliver Date: 26.05.2017
Class: Package services
Service(s): Delivery Confirmation
Status: eNotification sentDownload detailed reference about the purchase.
http://dhldeliverymailservice.com/documentdir/9793745186
To check on the delivery status of our mailing or arrange re-delivery
please visit our site.2017 DHL Corporation
*** This is an automatically generated mail, please do not reply ***
Other delivery methods may include infected software bundles that represent hacker-modified installers. They are usually spread on malicious download portals and P2P networks like BitTorrent. The LOCKER-PAY virus can also be spread via web scripts, ad networks and related threats. One of the most popular ways of getting infected with LOCKER-PAY virus is by coming in contact with a browser hijacker. This is a malicious browser extension that modifies essential settings when during the initial infection. In general they are used to cause several malicious actions:
- Redirect Users ‒ The browser add-ons change the default home page, search engine and new tabs page to direct to a hacker-controlled site.
- Malware Infection ‒ The LOCKER-PAY virus can be inserted into the victim’s computer as part of the infection chain.
- Computer Modification ‒ The malicious browser extension can change other settings such as the Windows Registry.
Related: .726 Virus, .725 Virus
Infection Flow of LOCKER-PAY Virus Virus
The initial code analysis shows that the virus is not related to any known of the famous malware families. Upon infection it follows a straightforward infection pattern. It may engage in the following behavior:
- Windows Registry Modifications ‒ The virus engine can cause dangerous modifications to the Microsoft Windows registry. This can lead to performance issues, problems with startup and other critical problems.
- Persistent Installation ‒ Certain versions of the LOCKER-PAY virus can institute a persistent presence on the affected machines. They can actively counter manual removal attempts.
- Additional Malware Delivery ‒ Infections caused by LOCKER-PAY can lead to delivery of other malware.
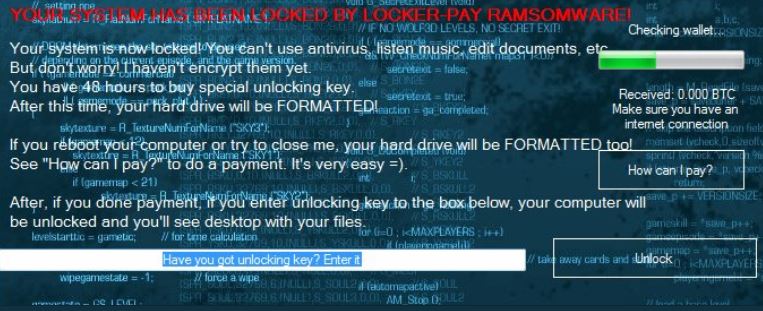
As soon as the preliminary infection is complete a lockscreen is instituted on the infected machines. It shows a message that blocks ordinary computer interaction with the computer until the virus is completely removed. It reads the following:
“YOUR SYSTEM HAS BEEN LOCKED BY LOCKER-PAY RAMSOMWARE!
Your system is now locked! You can’t use antivirus, listen music, edit documents, etc.
But don’t worry! I haven’t encrypt them yet.
You have 48 hours to buy special unlocking key.
After this time, your hard drive will be FORMATTER!
If you reboot your computer or try to close me, your hard drive will be FORMATTER too!
See “How can I pay?” to do a payment. It’s very easy =)
After, if you done payment, if you enter unlocking key to the box below, your computer will be unlocked and you’ll see desktop with your files.”
The hackers opt to use a blackmailing technique in order to make the victims pay them money.
You can efficiently remove the virus by following our removal instructions below.
Remove LOCKER-PAY Virus and Restore Data
WARNING! Manual removal of LOCKER-PAY Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
LOCKER-PAY Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover LOCKER-PAY Virus Files
WARNING! All files and objects associated with LOCKER-PAY Virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD LOCKER-PAY Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



