The .Master File Virus is a new iteration of the BTCWare ransomware family that has been identified in an ongoing attack campaign. The evolved threat encrypts data based on a predefined list of file type extensions and renames it with the .master extension. As usual the hackers behind it extort the victims to pay a fee in the Bitcoin digital currency. Our complete .master virus removal guide shows how the virus can be eliminated from the affected computers and all files restored.
Manual Removal Guide
Recover .Master File Virus Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does .Master File Virus Infiltrate the System?
The primary infection strategy used by the creators of the .master virus is the use of email phishing messages. The criminals use social engineering tricks to make the victims install the file attachments or hyperlinks containing the malware.
Infected office documents or software installers can also deliver the .master virus to the targets. They contain malicious scripts that install the .master ransomware downloaded from a remote server.
Malicious browser addons, also known as hijackers, can deliver the virus during their execution. They endanger the privacy of the users by harvesting sensitive data (including stored history, passwords, bookmarks and form data) and redirect the victims to a hacker-controlled site. Using such download redirects, web scripts and even ad networks the .Master File Virus (BTCWare Ransomware) can be delivered to a large number of users in a very short time.
Direct hacker attacks are also possible. Hackers seek out outdated software installations and attempt to exploit the weaknesses.
Related: OnyonLock Virus, Cryptobyte Ransomware
Infection Flow of .Master Virus
Security analysts detected an updated version of the infamous .master virus. The BTCWare ransomware family associated with it contains a lot of different variants that all share the same source. This new appearance shows that the criminals continue to develop the code base. Ever since its first inception, BTCWare virus ransomware was noted for its modular structure – the .master virus can easily be modified and built upon.
Like its predecessors, the BTCWare ransomware family starts its encryption engine after the infection is complete.
It is possible that some of the ongoing malware samples can modify essential Windows files and settings. Prior BTCWare virus samples were found to modify and add files to locations including the following: %AppData%, %Roaming%, %Local%, %LocalLow% and %Temp%. Changes made in these folders can have dire consequence on the affected machines – from the loading of additional programs and malware to slowdowns and even application loading failure.
The .master file virus modifies registry entries, Windows startup options and other essential configuration before proceeding with the encryption process. Some of the samples have been found to delete all found Shadow Volume Copies on the computers. This essentially prevents data recovery without the use of a high quality solution.
Once all preliminary actions are made the encryption process is started. The .master file virus encrypts user and system files based on a predefined list of file type extensions. They can be customized based on the attack wave. Prior samples processed the following files:
.1c, .3fr, .accdb, .ai, .arw, .bac, .bay, .bmp, .cdr, .cer, .cfg, .config, .cr2, .crt, .crw, .css, .csv, .db, .dbf, .dcr, .der, .dng, .doc, .docm, .docx, .dwg, .dxf, .dxg, .eps, .erf, .gif, .htm, .html, .indd, .iso, .jpe, .jpeg, .jpg, .kdc, .lnk, .mdb, .mdf, .mef, .mk, .mp3, .mp4, .mrw, .nef, .nrw, .odb, .ode, .odm, .odp, .ods, .odt, .orf, .p12, .p7b, .p7c, .pdd, .pdf, .pef, .pem, .pfx, .php, .png, .ppt, .pptm, .pptx, .psd, .pst, .ptx, .r3d, .rar, .raw, .rtf, .rw2, .rwl, .sql, .sr2, .srf, .srw, .tif, .wb2, .wma, .wpd, .wps, .x3f, .xlk, .xls, .xlsb, .xlsm, .xlsx, .zip
The .master ransomware like prior viruses acts against a wide range of data – archives, backups, photos, videos, configuration files, application data, images, documents and etc. The .master extension is added to all processed files. The .Master file virus engine can also modify the extension based on a template that includes the ransomware contact address as an prefix. This means that files can be renamed with master or .[[email protected]].master for example.
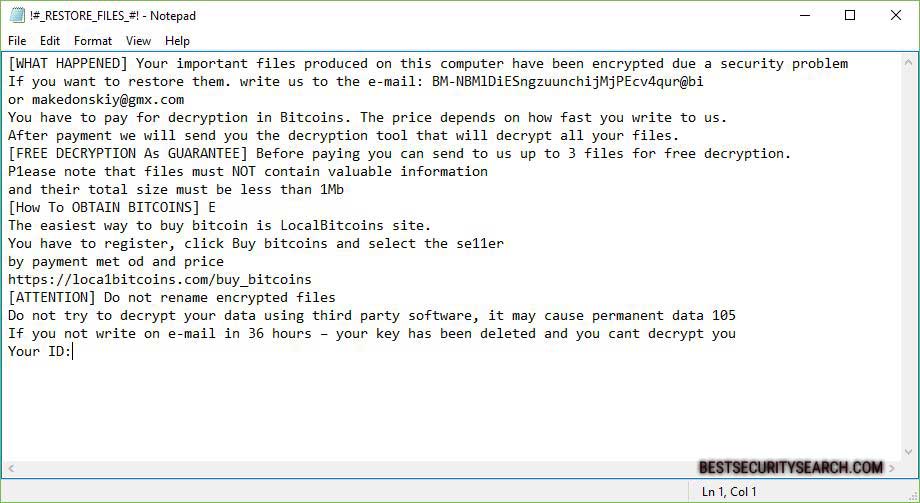
A ransomware note is crafted in a “!#_RESTORE_FILES_#!.inf ” file. This extension is usually mainly for configuration files and reads the following:
[WHAT HAPPENED] Your important files produced on this computer have been encrypted due a security problem
If you want to restore them. write us to the e-mail: BM-NBMlDiESngzuunchijMjPEcv4qur@bi
or [email protected]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION As GUARANTEE] Before paying you can send to us up to 3 files for free decryption.
P1ease note that files must NOT contain valuable information
and their total size must be less than 1Mb
[How To OBTAIN BITCOINS] E
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the se11er
by payment met od and price
https://loca1bitcoins.com/buy_bitcoins
[ATTENTION] Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data 105
If you not write on e-mail in 36 hours – your key has been deleted and you cant decrypt you
Your ID:
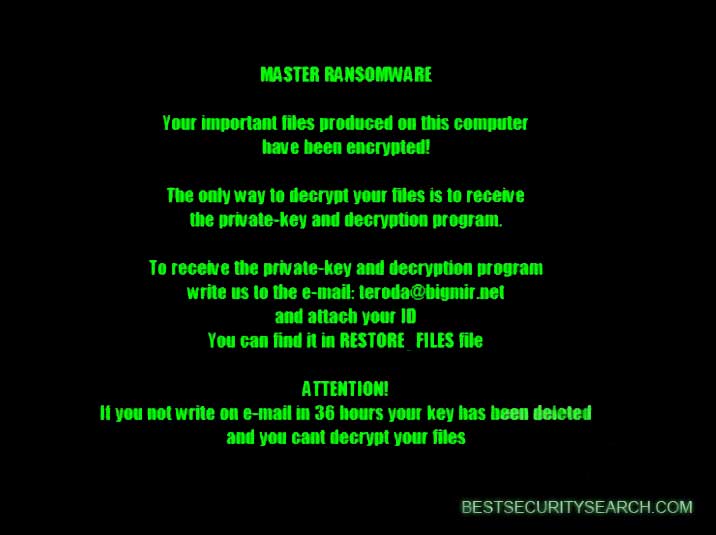
Some samples may display a lockscreen with green text on a black background that reads the following message:
MASTER RANSOMWARE
Your important files produced on this computer have been encrypted!
The only way to decrypt your files is to receive the private-key and decryption program.
To receive the private key and decryption program write us to the e-mail: [email protected]
and attach your ID
You can find it in RESTORE_FILES fileATTENTION
If you not write on e-mail in 36 hours your key has been deleted
and you cant decrypt your files
The .Master file virus has also been found to delete Shadow volume copies, modify important Windows files and conduct other malicious actions as part of its behaviour pattern.
Some of the prior BTCWare virus samples were found to initiate network communication with the criminals via remote servers operated by the hackers. This fact means that future or modified versions of the BTCWare ransomware can be used to steal data or remote control the machines.
Refer to our in-depth removal guide to restore your computer and recover your data in a safe manner.
Remove .Master File Virus and Restore Data
WARNING! Manual removal of .Master File Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
.Master Virus (BTCWare Ransomware) – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .Master File Virus
WARNING! All files and objects associated with .Master File Virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD .Master Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



