The new version of the Cerber ransomware virus, Cerber3 surfaced on the web in late August. The virus lives up to its name and has infected a lot of users since it appeared. The virus remains encrypted, and infected users have no way to decrypt their files except to wait for a decryptor or pay the crooks.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Since our last article on Cerber3, the virus has infected a lot of users. Google Trends shows that the searches for the ransomware have increased drastically in since September 12.
Chart of the Cerber3 Searches:
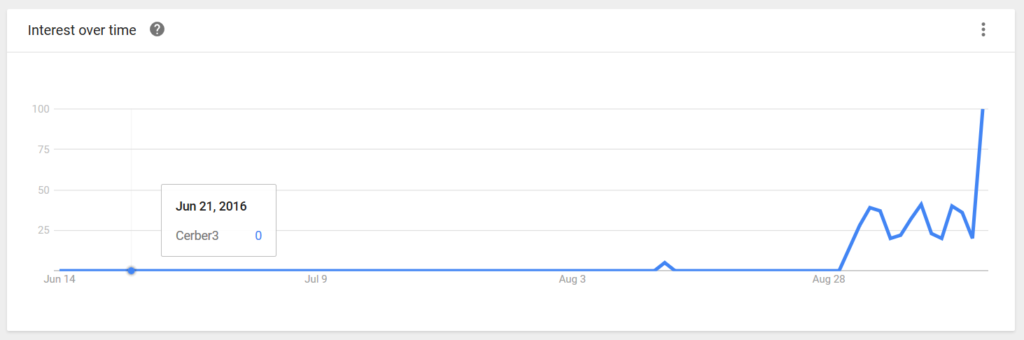
Our site registers more traffic to the third Cerberarticle written when the virus first appeared.
Increasing Infections of Cerber3.
The reason behind the growing number of infections may be due to Cerber3’s infection methods. The new version of the ransomware has improved infecting capabilities, including an expansion of the malvertising campaign that spreads Cerber V3. Experts at Enigma Software have also studied the virus’s infection methods.
They have this to say :
To make matters worse, the spreading matrix of Cerber3 has expanded where it uses malvertising exploits through RIG and Magnitude exploit kits. Such exploit kits are known for aggressive spam campaigns that carry malicious attachments using JavaScript code to install ransomware.
Cerber3 Virus – The Hell-hound of the Ransomware World
While Cerber 1 was decrypted, the cybercriminal collective behind the virus quickly created a new version, which rendered decryptor tools useless.
The Cerber ransomware family is very dangerous. The cybercriminals behind it are seasoned veterans with a lot of money and time to make their viruses as dangerous as they can be. That’s a sure way to launch their ransomware to the top of the food chain. According to one report, Cerber infects in 201 countries around the world.
The third Cerber is the most dangerous virus of the family. According to Enigma Software:
Ultimately, Cerber3 will never allow decryption of files that were decrypted and tagged with a .cerber3 file extension no matter how much money you want to throw at its authors or perpetrators.
That’s pretty low, even for ransomware scammers. After all, why would people pay if they knew that they wouldn’t receive their files back? Sadly, people will probably continue to pay, even though its against what most cyber-security experts would advise.
Cerber3 Ransomware Virus – What Comes Next?
If your computer was infected with Cerber3, you should remove the virus using anti-malware tools. That won’t decrypt your files; you’re going to have to wait for a decryptor to be released. To prevent this from happening in the future, make frequent backups of your important files. Don’t let cybercriminals have their way with you and your computer. Also, don’t pay them, as the Cerber3 team won’t decrypt your files.
A new version of the Cerber family could be developed in the near future. Everyone should watch out and take the necessary measures to protect their computer from the threat.
The Cerber virus continues to evolve. The newest trick used by the scammers is the random extension. Previous Cerber variants used the .cerber/.cerber2/.cerber3 but now the extensions are random four character combination.
The new random infection was dubbed .bed5 Cerber ransomware virus.
Another new version of Cerber also went live earlier in October 2016. This infection was named Cerber 4.It also used random extensions similar to .bed5.
The random extension makes it more difficult for users to search for a solution via search engines.



