Celebrities Nude Photos and Videos leaked in a new major data dump dubbed “The Fappening 2.0” on various Internet communities.
The Fappenning 2.0 Leak Revealed
Brazzers Hacked – Close to a Million Users Affected
Hundreds of personal photos of celebrities are now being distributed by Internet users in various online communities ranging from forums to places like Reddit and the infamous 4Chan image board. This incident is very similar to the last major leak known as “The Fappening” which occurred several years ago. The current leak has appeared on the Internet since Tuesday and the contents is comprised mainly of photos taken by the celebrities that range from simple selfies to sexually explicit photos. According to several screenshots found online in the next few days new images will be released on the various sites. This indicates that a potentially large leak has occurred.
This has been proven to be a legitimate concern for the affected celebrities as a representative for Emma Watson confirmed that stolen photos of the actress have appeared online and are legitimate. Their explanation is that the photos are made in a photo shoot and do not feature sexually explicit content. Emma Watson is shown posing in various outfits and fully clothed. Along with them in the data dump sets there are images of her posing nude in a bathtub which however have not been confirmed officially. Other famous stars include Amanda Seyfried and Jillian Murray. A newer set contains sexual footage of Rose McGowan (actress), Alyssa Arce (model), Katie Cassidy (actress), Rhona Mitra (actress), Iliza Shlesinger (comedian), Analeigh Tipton (figure skater and actress), Paige (WWE star), Dylan Penn (model), Kristianna Loken (actress), Trieste Kelly Dunn (actress), April Love Geary (model) and Lili Simmons (actress). Like the previous incident we suspect that the main cause lies in a security issue that has been exploited by criminals. As the content seems to be made by mobile devices (smartphones and tablets) the problem may lie in a vulnerability in a widely used app or bug in the operating system itself.
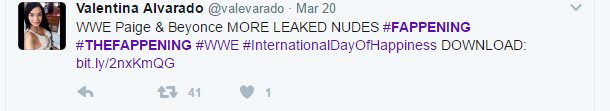
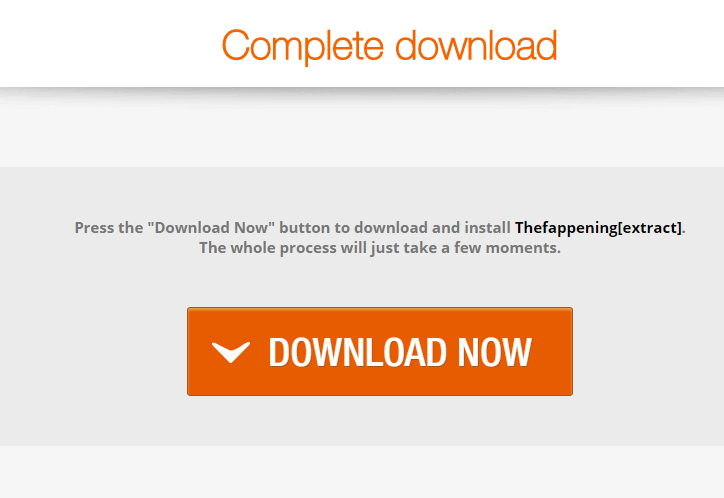
The hackers behind The Fappening 2.0 promise to release new content in the coming days and even cite some specific stars including Jennifer Lawrence, Kylie Jenner and Marisa Tomei. As the leak has lead to massive popularity online various malicious groups have taken the time to craft scams that take advantage of curious users by placing scam email links (usually using URL shortening services and dangerous redirects) to point the targets into infecting themselves with malware disguised as data dumps or “viewing apps”. In most cases the hackers use counterfeit or hacked user profiles to spam the relevant social media or internet community with the hyperlinks. They lead to dangerous malware infections which can infect the victims with the latest ransomware threats. At the moment there are several distinct scam campaigns that are active:
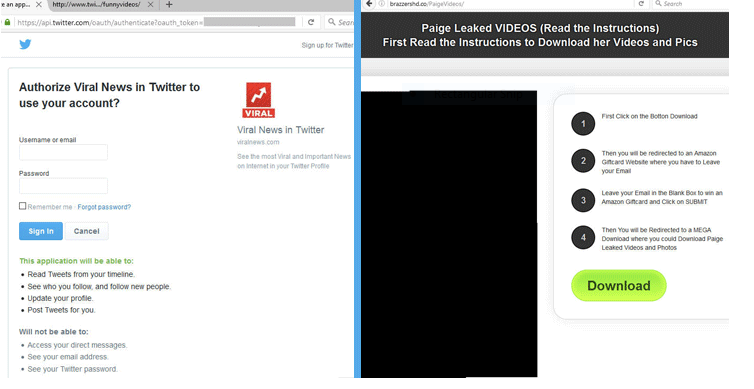
- Twitter Spam Bots – A large-scale botnet network of hacker-controlled accounts on Twitter post links that post links that pose as hosting sites that contain data dumps promising to contain the lucrative contents. In many of the observed cases they present the users with the option of installing an app called “Viral News” which promises access to the photo sets. The victims are made to give the malicious application permission to access their Twitter profile which can tweet on their behalf and change the profile’s setting. The outcome of this attack is that the criminals can potentially take over control of the accounts.
- Malware Redirects – The various online communities are spammed with malicious redirects which can either lead to a virus infection via the download of a malware. Other cases install browser hijackers or leads the victims to a hacker-controlled ad-network which generates revenue for them.
- Counterfeit Content – As some of the photos do not show the face of the depicted celebrity malicious users can create counterfeit images.
It has been confirmed that around 7000 users have become victim to this scam according to one of our sources. To protect yourself from abuse and malware infections you can follow these security tips:
- Don’t Reuse Old Passwords – One of the main causes of hacker intrusions is by reusing old passwords. Database breaches and account leaks are a widely used repository for any information pertaining to computer targets which are often cross-linked when attacks are considered. Security experts advise users to use long and complex passwords.
- The Use Of Two-Step Authentication – Identity validation through two-step authentication can remedy against some of the possible attacks.
- Don’t Download Files From Untrusted Sites – Even if a legitimate data dump is accessible, the users need to check if they are hosted by a legitimate file hosting service as some of them use a virus checker that is automatically engaged.
- Check The Provided Links – All links that are comprised of suspicious domains, URL shortening services and related untrusted areas should be avoided.
- Don’t Explicitly Trust Your Friends – Usually when such large-scale incidents happen the hackers can take control of many victim accounts including those of people in your friends list. Don’t explicitly trust them, especially when they share links or files in a sudden and suspicious way.
- Use Only Official App Repositories – App downloads should only be made through the official and legitimate app repository for the relevant platform. This is especially true for mobile operating systems (Android and iOS) where malware usually lurks in popular third-party software managers, repositories and sites.
- Link Checking – Before accessing any hyperlink use the mouse to check for the destination site and make sure that it doesn’t lead to an untrusted location.
We recommend that all users use a quality ant-malware solution which protects the computers against all forms of viruses (Trojans, ransomware, hijackers, redirects and etc.) and can remove active infections with a few mouse clicks.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



