Oops ransomware virus is designed to encrypt valuable data stored on the infected machine and demand a ransom of 0.1 BTC. It marks corrupted files with the .oops file extension and renders them completely unusable. Then it displays a ransom note which provides decryption instructions. Infected users can regain PC security by removing the threat. Afterward, alternative data recovery approaches could help for the .oops files restore.
Manual Removal Guide
Recover .oops Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
More Details About Oops Ransomware Virus
Oops is a new data locker ransomware that has been spotted in the wild. Ransomware is a type of malware that modifies the original code of target files via strong cipher algorithms like AES or RSA. As a result, corrupted data receives the malicious file extension .oops and gets out of order. Oops ransomware is designed to scan for target file types and encrypts them. The threat seeks to encrypt files with the following extensions:
.doc, .docx, .xls, .xlsx, .jpg, .png, .txt, .ppt, .pptx
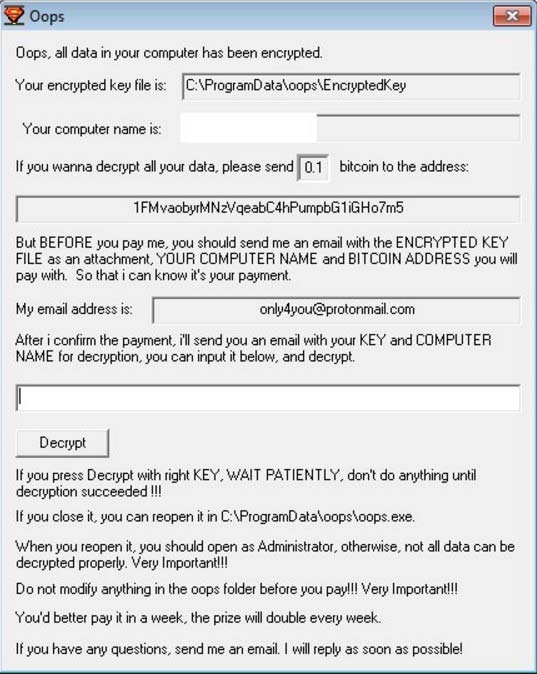
As soon as the ransomware encrypts files it displays a ransom note on the PC screen. The text on it provides instructions on ransom payment. Hackers demand from victims to make a transaction of 0.1 Bitcoins to a predefined payment address in exchange for the decryption key. The whole message reads:
Oops
Oops, all data in your computer has been encrypted.
Your encrypted key file is: C: \PrograrnData\oops\EncryptedKey
Your computer name is:
If you wanna decrypt all your data, please send 0.1 bitcoin to the address:
1FMvaobyrMNzVqeabC4hPumpbG1iGHo7m5
But BEFORE you pay me, you should send me an email with the ENCRYPTED KEY FILE as an attachment, YOUR COMPUTER NAME and BITCOIN ADDRESS you will pay with. So that i can know it’s your payment.
My email address is: [email protected]
After i confirm the payment, i’ll send you an email with your KEY and COMPUTER NAME for decryption, you can input it below, and decrypt.
Decrypt
If you press Decrypt with right KEY, WAIT PATIENTLY, don’t do anything until decryption succeeded I!!
If you close it, you can reopen it in C:\ProgramData\oops\oops.exe.
When you reopen it, you should open as Administrator, otherwise, not all data can be decrypted properly. Very Important!!!
Do not modify anything in the oops folder before you pay!!! Very Important!!!
You’d better pay it in a week, the prize will double every week.
If you have any questions, send me an email. I will reply as soon as possible!
How Does Oops Ransomware Infect Computers?
As the Ooops ransomware infection is generally triggered by a single executable file, that file may be embedded in word document as a malicious macro. This method allows the ransomware payload to start once the document is opened on PC with enabled macros in the Office pack. The payload may also be hidden as JavaScript code in PDF documents or injected into web pages. These compromised components can be then included in spam email campaigns that use engaging message making users more inclined to interact with them. Usually cyber criminals attach the compromised files to the email, provide a link in the text body or display button with download option. Beware even if the email sender seems to be legitimate because most of registered cases of ransomware attacks prove that this approach is preferred by hackers. The so-called bundling is another distribution method that may be used for Oops ransomware virus distribution. In this case the malicious code is included in the installation set of various freeware programs whose authors do not disclose properly what goes along with the primary software. As hackers are constantly seeking for new lucrative distribution techniques the ransomware may be stalking online users almost everywhere – emails, social media, advertisements, various websites, free software, torrent files, etc.
Related: How To Restore .malki Files, Reyptson Ransomware Removal Guide
Remove Oops Ransomware Virus and Restore Data
WARNING! Manual removal of Oops Ransomware Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Reyptson Ransomware Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .oops Files
WARNING! All files and objects associated with Oops ransomware should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD Malki Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



