Encryption methods for Gnu/Linux allow computer owners to protect their stored data in a safe manner. Depending on the encryption method users can experience different levels of protection and performance. Different tools and system utilities are used depending on the method. In this article, we are taking an overview of the available techniques.
Encryption types in Linux systems
Encrypting user and system data helps protect Gnu/Linux systems from unauthorized access. This method of file protection uses cryptography methods to encrypt (secure) the chosen data and only decrypt (allow access) to users who successfully authenticate with the system in a prescribed manner. Common scenarios include the protection of sensitive data from non-trusted people when physical access is available. This means that even by stealing or copying the contents of the device, the files still cannot be accessed by malicious users. Lost or stolen laptops, netbooks or external hard drives and flash drives with good encryption applied will not allow access to the files. Many companies or individuals who hold sensitive information may opt to encrypt or store away their private information before sending their computer to the repair shop for upgrade or repair services.
However, cryptography does not prevent damage from all computer crimes. Victims are still vulnerable to attacks upon infection of unlocked files. Physical access can still be gained by criminals if they can launch a cold boot attack, essentially retrieving the master keys from a running system. The two other types of risk are associated with social engineering and brute force attacks. The later are effective only against cryptography methods with weak ciphers.
A strong encryption setup is the best defense against malicious attacks targeted against sensitive data.
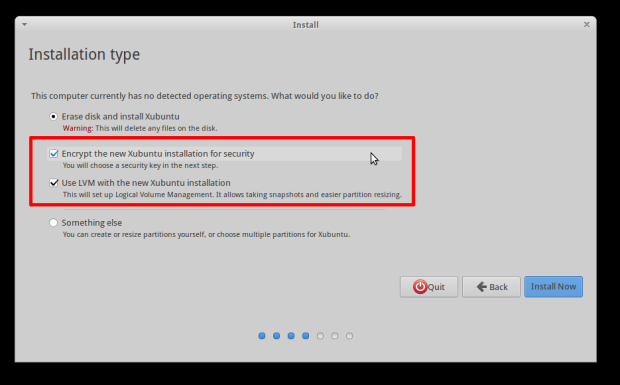
There are two main encryption setups that Linux users can use:
- Data encryption
- System encryption
This setup encrypts the whole contents of the device – both the operating system, any system partitions and all user data. The main disadvantage is system performance. The chosen encryption setup must secure all files, memory access, and connected devices. Also unlocking the computer with the chosen type of passphrase or another method may be impossible if the access means are lost. Disk encryption works in a way that integrates in a compatible manner to the operating system and the user applications. The user is prompted to authenticate himself/herself with a secure method (a token or a passphrase) and then the protected area (the user data or the whole system) is “unlocked”.
In essence, this type of protection secures only the user data – the /home directory or mount point and all locations that the users can access with their permissions. Modern Gnu/Linux distributions utilize many daemons and user-land utilities that work with the user data like caching and thus hashes, parts or links to files and folders may also be stored in other locations of the computer file system such as the /swap partition used for virtual memory, the /tmp partition for temporary files created by user applications and the /var partition typically used for log files, databases, and other miscellaneous cases.
There are ways to modify the system behavior in providing better security options for protecting the system security when using solely data encryption in case of possible attacks or fears of physical unauthorized access. Examples include the disabling of the swap or using cryptography methods for securing the virtual memory as well. Temporary files can be accessed from a ramdisk and indexes, and log files can be stored in the users /home folder when appropriate configuration has been made.
Additionally there are two main types of encryption based on the layer of operation:
- Stacked file system encryption – encryption is used as a layer that works on top of the existing file systems. This method causes all files written to an encrypted location to be secured on-the-fly before the data is written to the disk. Whenever information is accessed, it is encrypted when a read operation is executed. All files and folders in the encrypted location are stored in an encrypted form. The user unlocks the folder with the raw encrypted files in the file system with the correct passphrase. The data is the mounted using a special pseudo-filesystem onto itself or in a different location where the available data is available in a readable form. Data access is denied upon the unmounting of the pseudo-filesystem, specific power event or another type of encryption interruption.
- Block device encryption – this encryption method utilizes encryption below the file system layer, assuring that everything is written to a specific encrypted block device (a hard disk, system partition or a file acting as a virtual loop-back device). While the secured container is offline (no access is granted) its data contents appear as random data – there is no way of determining the type of file system and the data that it contains. Access is made by mounting the block device and decrypting its contents.
Preparing Your Linux System for Encryption
Before considering disk or file encryption, it is a good idea to perform a low-level zero overwrite to the hard disks. This not only secures all data in a secure way but also prevents system utilities from recovering data that was available prior to the encryption. Obviously, this will delete all contents from the selected drive so a secure backup must be made. This secure wipe also prevents disclosure of commonly used access patterns (read and write operations) of the users and the installed system applications and utilities.
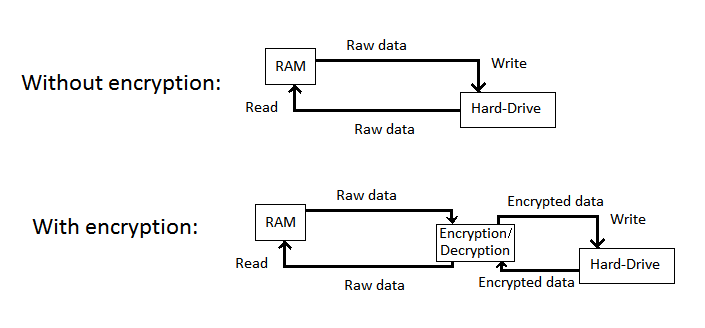
Encryption is utilized when each block device (in the case of block device encryption) or file (in the case of stacked file system encryption) is divided into sectors of equal length. The encryption and decryption processes operate on a per-sector basis. When an application or the operating system accesses a sector fragment, the whole sector that contains the data is decrypted and stored the system’s memory.
Decryption is possible only a master key (or passphrase) is present to the computer. This key may be stored in a plain text file, in a protected form or randomly generated on-the-fly depending on the method and configuration. Two-factor authentication can be provided for additional security by storing the key in a secure location.
The algorithm used is called a cipher, popular variants include Blowfish, AES, Twofish.
Most popular Gnu/Linux distributions provide easy ways of enabling encryption in their settings utilities. Refer to the provided documentation for more information on setting up encryption.