Our removal guide shows how computers can be restored from the Bitpaymer virus, a ransomware that marks files with the .locked extension.
Manual Removal Guide
Recover Bitpaymer Virus Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does Bitpaymer Virus Infiltrate the System?
Bitpaymer Virus infections can be acquired by falling victim to one of the criminal methods of distribution.
One of them is the use of spam emails. The criminals use template messages that resemble famous companies and products. The Bitpaymer Virus samples can be directly attached or linked in the body contents of the emails.
The criminals can attempt to include the ransomware code in payloads as well. The two most popular forms are documents and software installers. The documents can be of different file types – spreadsheets, rich text documents or databases. The hackers bundle malicious macros that when run by the victims download the malware from a remote server and execute it. Infected software installers are usually legitimate apps that were downloaded from legitimate sources, modified and then uploaded to hacker-controlled download portals.
In many cases the Bitpaymer ransomware can also be found be installed using browser hijackers by following the built-in infection patterns. They are malicious add-ons that change the configuration settings of the most popular web browsers: Mozilla Firefox, Google Chrome, Microsoft Edge, Internet Explorer, Safari and Opera. Their aim is to point the victims to a hacker-provided address by changing the default home page, new tabs page and search engine.
Bitpaymer Virus can be hosted on hacker-controlled download sites or P2P networks where pirate content is usually found.
It is also possible to attain an infection after a direct hacker intrusion. Such attacks are usually done using automated kits that seek out vulnerable software or operating system services. Lately the majority of attacks are usually done against remote control servers and installations.
Related: Remove DCry Virus and Restore .dcry Encrypted Files, Remove The AdWind Virus Infections and Restore Your Computer
Infection Flow of Bitpaymer Virus
Bitpaymer Virus is a newly discovered ransomware that has just been identified by security researchers in a new attack campaign.
During the initial analysis it did not showcase any code similarities with any of the famous malware families, nor the identity of the hacker or criminal collective behind it. We suspect that the Bitpaymer Virus is an original threat. It bears a fake copyright “Microsoft Corporation” which may confuse some of the users that attempt to investigate the binary file. The virus automatically copies itself to several system folders soon after the infection has been initiated.
Before proceeding with the ransomware actions it performs several important checks that are built into the code. The ransomware engine uses harvested information from the victim computer as input values during the encryption phase. This is the reason why a large quantity of sensitive data is obtained: unique cryptographic machine ID, Microsoft Windows installation date, important configuration files and user language settings.
The user language settings are used by the hackers to obtain information about the location and preferences of the victims. Further updates of the Bitpaymer Virus may include ransomware notes in several languages. If the regional language settings show a match then that note will be displayed to the victims.
Other malicious actions of note include the Bitpaymer Virus’s ability to create, modify and delete registry entries. This is used both for modifying the computers and for attaining a persistent state of installation. This allows the Bitpaymer Virus engine to actively monitor for any manual removal attempts. Effective removal of the ransomware is only possible by using a quality anti-spyware solution. Refer to our instructions for an easy solution to this problem.
Bitpaymer Virus can delete system files as well that can lead to performance issues or even computer boot failures. The criminals have included a hijacker code that modifies the settings of web browsers. It is possible that this code can affect multiple of the most famous web browsers: Mozilla Firefox, Google Chrome, Microsoft Edge, Internet Explorer, Safari, Opera. This relays the network traffic through hacker-controlled gateways that can be used both to spy on the victims and also to allow for identity theft and other crimes. Additional malware can be installed by utilizing web scripts redirects and other related sources.
Bitpaymer Virus can initiate its own processes and read the status of the victim computers. This is used to harvest information about both user installed programs and system services. The virus engine can modify system services, the captured Bitpaymer ransomware samples were detected to modify the network configuration.
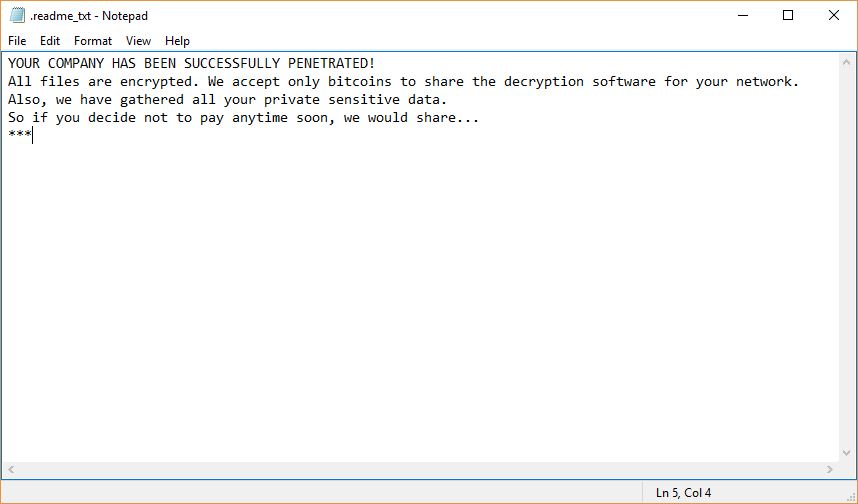
The Bitpaymer Virus launches its ransomware module soon after the initial checks are done. A ransomware note is crafted in a “.readme_txt” that reads the following message:
YOUR COMPANY HAS BEEN SUCCESSFULLY PENETRATED!
All files are encrypted. We accept only bitcoins to share the decryption software for your network.
Also, we have gathered all your private sensitive data.
So if you decide not to pay anytime soon, we would share…
***
The collected Bitpaymer Virus samples append the .locked extension that is used mainly by the Hidden Tear family. The ransomware note points to a network address located on the TOR hidden network. The victims are instructed to down the special web browser that is required to access it.
The hacker-operator Bitpaymer virus gateway requires the users to enter their unique victim ID in a string appended to the address. Inputting a blank or incorrect payment ID results in an error message.
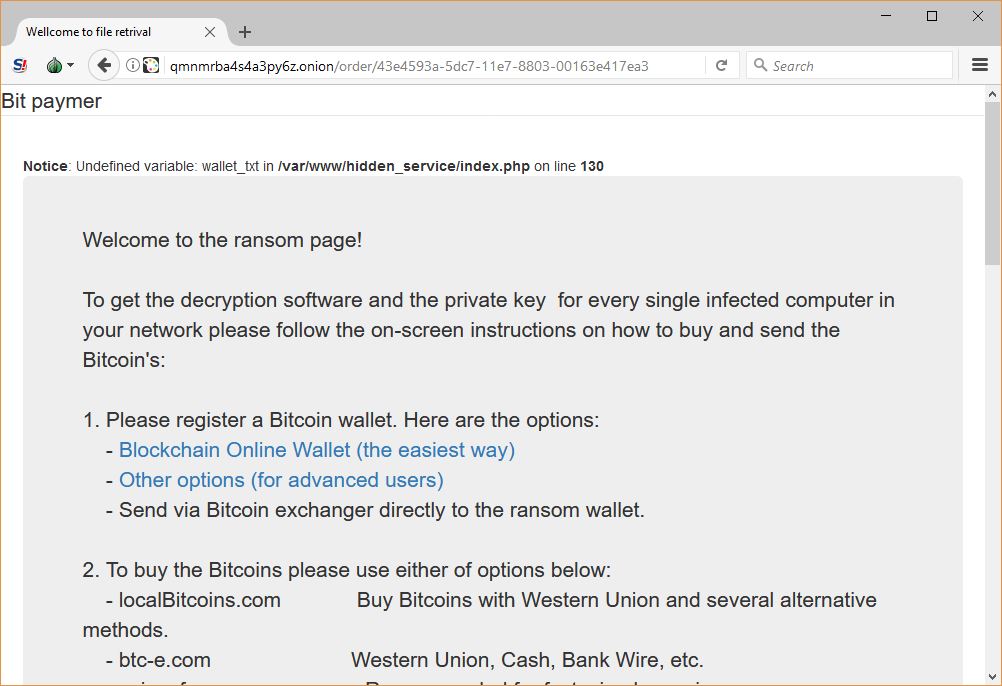
Once this is done they are shown the gateway which reads the following message:
Welcome to the ransom page!
To get the decryption software and the private key for every single infected computer in your network please follow the on-screen instructions on how to buy and send the Bitcoin’s:
1. Please register a Bitcoin wallet. Here are the options:
– Blockchain Online Wallet (the easiest way)
– Other options (for advanced users)
– Send via Bitcoin exchanger directly to the ransom wallet.
2. To buy the Bitcoins please use either of options below:
– localBitcoins.com Buy Bitcoins with Western Union and several alternative methods.
– btc-e.com Western Union, Cash, Bank Wire, etc.
– coincafe.com Recommended for fast, simple service.
– coinbase.com Western Union, Bank of America, Cash by FedEx, Moneygram, Money Order. In NYC:
Bitcoin ATM, in person.
– localBitcoins.com Service allows you to search for people in your community willing to sell Bitcoins to you directly.
– cex.io Buy Bitcoins with VISA/MASTERCARD or wire transfer.
– btcdirect.eu The best for Europe.
– bitquick.co Buy Bitcoins instantly for cash.
– howtobuyBitcoins.info An international directory of Bitcoin exchanges.
– cashintocoins.com Bitcoin for cash.
– coinjar.com CoinJar allows direct Bitcoin purchases on their site.
– anxpro.com
– bittylicious.com
3. Get bitcoin wallet for payment (bitcoin address valid for 12 hours, if 12 hours passed please get the new wallet)
4. Send 50 BTC to the bitcoin address
15G6YvWH9hFp6BetJdVs4xgsx2wyimcHc1 (must be sent in 1 transaction!)
Please note that we require 3 Bitcoin transaction confirmations.
– To view the current status of your transaction please follow the link:
https://blockchain.info/address/15G6YvWH9hFp6BetJdVs4xgsx2wyimcHc1
– Once the transaction passed 3 confirmations please refresh the page and you will be granted to download the decryption software
– If something goes wrong please contact us via email: [email protected]
– We can decrypt 2-3 non-important light-weight files before you pay, send’em to email: [email protected]
4. Please be advised that the ransom amount may be raised after 48 hours since your first visit if no payment received.
In 7 days this link would be deleted, so all your information could be lost.
Your company is secure enough, but we may tell you what is wrong after payment being processed. Good Luck!
The gateway lists several exchanges where Bitcoins can be bought. The hackers behind the Bitpaymer Virus request a large ransomware fee from the victims – 50 Bitcoins to help them recover the files. This amount to about 116 000 US Dollars. The computer users must not pay the hacker, but utilize a quality anti-spyware solution.
Fortunately at the time of writing this article none of the victims have commited into paying. The Bitcoin digital currency operates anonymous transactions and is widely used by computer criminals to transfer money.
The criminal operators of the Bitpaymer Virus have decided to include a support email address that can be used to contact them. It is hosted on a secured service which means that it is likely to be used for blackmailing purposes as well. The hackers give the ability to decrypt two or three “lightweigh” files to demonstrate that they have the private decryption key. This is a popular tactic used by criminals to win the trust of the victims.
To effectively recover your computers from Bitpaymer virus infections follow the instructions below. We explain how to easy an easy to use quality anti-spyware solution that is able to remove the virus completely. All affected files can be recovered using the showcased data recovery software.
Remove Bitpaymer Virus and Restore Data
WARNING! Manual removal of Bitpaymer Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Bitpaymer Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Bitpaymer Virus Files
WARNING! All files and objects associated with Bitpaymer Virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD Bitpaymer Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



