We have prepared a complete removal guide for the victims of the launchpage.org browser hijacker which is a threat to the privacy of its victims.
Launchpage.org Browser Hijacker Description
The launchpage.org browser hijacker is a dangerous virus threat which is installed on victim computers through a malicious browser extension. It is compatible with the most widely used web browsers – Google Chrome, Mozilla Firefox, Safari, Internet Explorer and Microsoft Edge. Once installed it modifies essential settings of these application such as the default home page, default search engine and new tabs page. Other changes may include other modifications which can endanger ther users privacy.
Malicious extensions such as the launchpage.org browser hijacker are able to cause a lot of damage to the infected computers including the following:
- Redirection to Third-party Sites – The main objective of the browser hijackers are to lead the victims into hacker-operated sites by modifying essential settings.
- Operating System Security Modification – Some of the browser hijackers are able to modify the settings of the Windows operating system. As a result overall security is lowered, in some cases anti-virus software can be disabled.
- Additional Payload Delivery – Threats like the launchpage.org browser hijacker can be used to deploy other viruses to the infected computers.
The virus follows a predefined infection route which consists of the following steps:
- Initial Delivery – This is the point of intrusion into the victim computers. The computer users get infected with the virus through its various delivery methods.
- Browser Modification – The hijacker modifies the infected browsers by changing their settings to the hacker-specified values.
- Operation – The browser hijacker actively transmits user data and other sensitive information to the remote operators. This includes everything from bookmarks to stored form data, account credentials, web history and cookies.
We have been unable to identify the people behind the launchpage.org site as they have been hidden by their hosting provider. The page itself links to several popular online services and social networks that the victims may use. By navigating to them the hijacker can attempt to spy on their activity.
The launchpage.org browser hijacker may be distributed using various methods. At the moment we have not been able to confirm the main ones and we suspect that the hackers use multiple strategies. One of the most widely used ones is the email mass spam campaign. Hackers utilize various social engineering tricks to make the users infect themselves. Available options include directly attaching the browser hijacker as an attachment, sending a hyperlinked message in the body or using embedded scripts in infected files. Recently the use of counterfeit office documents has been used as a popular method for spreading all types of malware. The victims craft files that pose as being of user interest – invoices, letters, contracts and etc. Once they are opened a notification window prompts them for a macro execution. Once this is done the browser hijacker is delivered to the victims.
Malware such as this one can also delivered also via infected software installers. They are modified free or trial versions of popular applications, games, patches and etc. They are usually distributed alongside the launchpage.org binaries on hacker-controlled or hacked download sites. Other places where users can acquire the malware are P2P networks like BitTorrent where pirate content is usually hosted.
Possible Updates To The Launchpage.org Browser Hijacker
There are various types of browser hijackers. Depending on the type of malware a future update can include any of the following features:
- Rogue Application Presentation – Some types of browser hijackers create counterfeit notification prompts which aim to scare the victims into thinking that their computer has been infected by viruses. The hijackers redirect them to a product page or download portal where they are offered a solution.
- Endless Redirection – Browser hijacker typically redirect the users to hacker-controlled sites for various reasons. However some of them do this in a way which makes browsing practically impossible. Examples of such strains process all user queries through non-existent sites. As a result it is impossible to browser any site.
- Stealth Installation Hijackers – These hijackers attempt to show no sign of infection and attempt to hide themselves from the users as much as possible. They change the application settings to pass traffic through hacker-controlled sites however no obvious preferences are modified.
- Information Stealing Trojan Browser Hijackers – Advanced forms of browser hijacker can include code that is able to harvest sensitive information from the victims. This includes not only their stored account credentials, browsing history, cookies, preferences, saved form data and etc., but also files from their computers.
- Additional Payload Delivery – The malicious extension can be used to deliver viruses to the infected computer.
- Obtrusive Ads – The browser hijacker can directly display ads in various forms (text, graphics, in-page, hybrid and etc.) of paying customers. This tactic generates revenue for the hijacker operators based on the amount of infected victims and frequency of interaction with the advertised service.
- Performance Impact – Other types of malware can cause delibrate performance issues. This can include anything from slow-downs to application crashes and even operating system boot up problems.
- Security Software Bypass – Advanced hijackers are found to disable the installed security solutions. This means that the hijackers can be used as a first-stage infection in a complex malware installation attempt. This is particularly useful for ransomware.
- Persistent Installation – The virus can achieve a persistent state of execution which makes removal possible with the use of a quality anti-spyware solution.
- Identity Spoofing – A notable example of such behavior was a particular strain of browser hijackers which stole cookies that were used to conduct malicious activities. The hijacker used the cookie to install malicious Android app onto the user’s phone without their consent.
Using a quality anti-spyware solution Internet users can defend themselves against possible virus installations. All active threats can be removed using only a few mouse clicks.
Protect Yourself From Hijackers like Launchpage.org
To completely eliminate the threat we suggest that all infected users use a quality anti-spyware tool as it can both delete active infections with only a few mouse clicks and provide strong protection against all kinds of threats.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Launchpage.org browser hijacker Removal Guide
Manual removal of Launchpage.org browser hijacker requires being familiar with system files and registries. Removal of any important data can lead to permanent system damage. You could prevent this troublesome effect and delete Launchpage.org browser hijacker browser hijacker with SpyHunter malware removal tool.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the browser hijacker so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Remove Launchpage.org browser hijacker from Windows
Here’s a way to remove the program. This method will work regardless if you’re on Windows 10, 8, 7, Vista or XP. Simply selecting the program and pressing delete won’t work, as it’ll leave a lot of small files. That’s bad because these leftovers can linger on and cause all sorts of problems. The best way to delete a program is to uninstall it. Here’s how you can do that:
- 1) Hold the “Windows” button (It’s between CTRL and Alt on most keyboards) and press “R”. You’ll see a pop-up window.
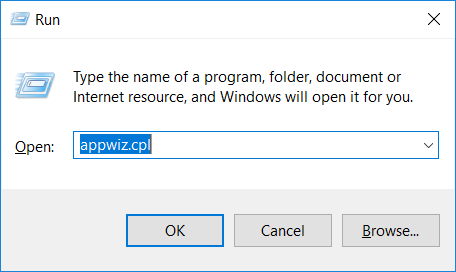
- 2) In the textbox, type “appwiz.cpl”, then press“ Enter ”.
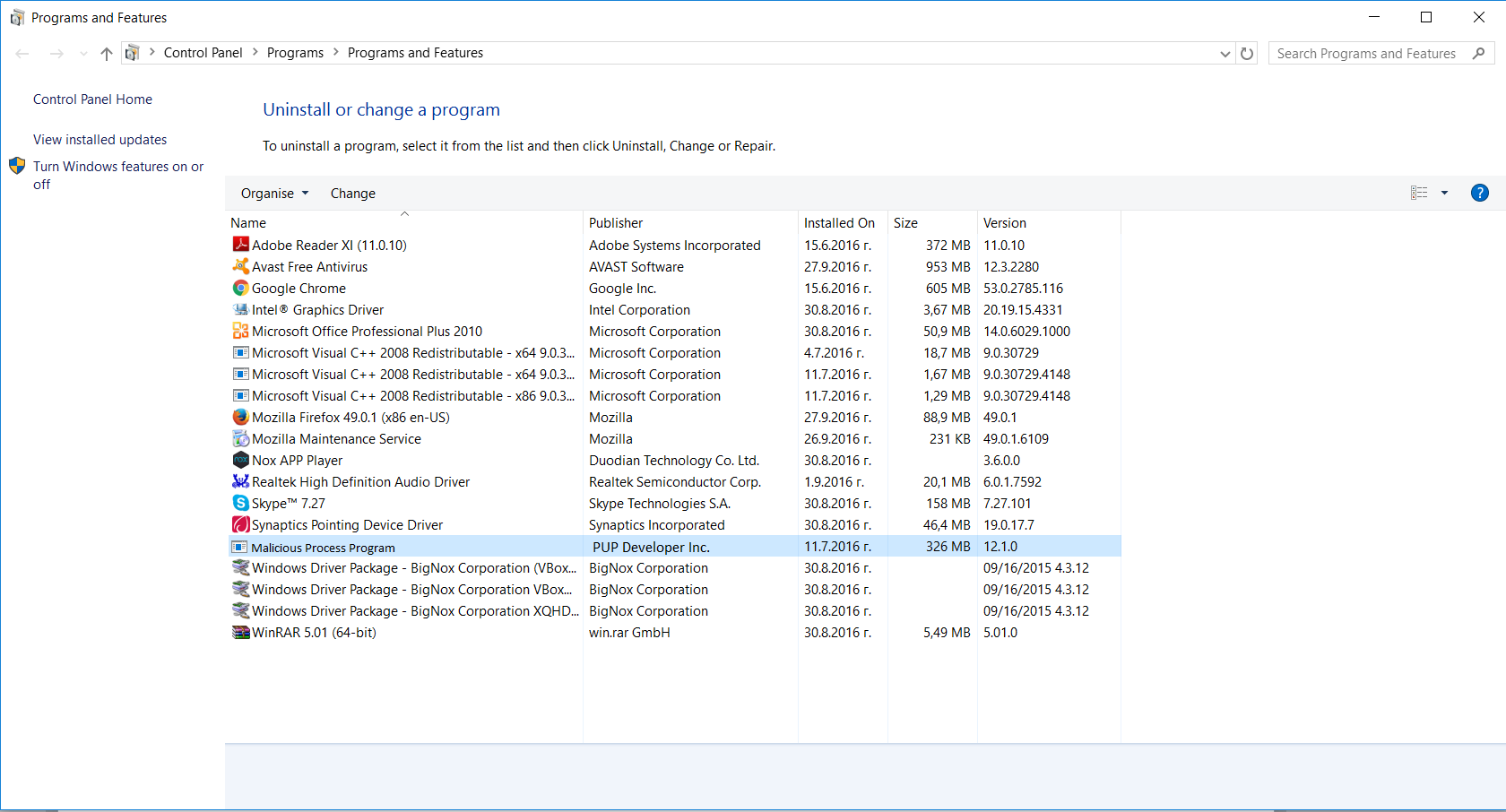
- 3) The “Programs and features” menu should now appear. It’s a list of all the programs installed on the PC. Here you can find the program, select it, and press “Uninstall“.
STEP III: Remove Launchpage.org browser hijacker From Your Browser
Before resetting your browser’s settings, you should know that this action will wipe out all your recorded usernames, passwords, and other types of data. Make sure to save them in some way.
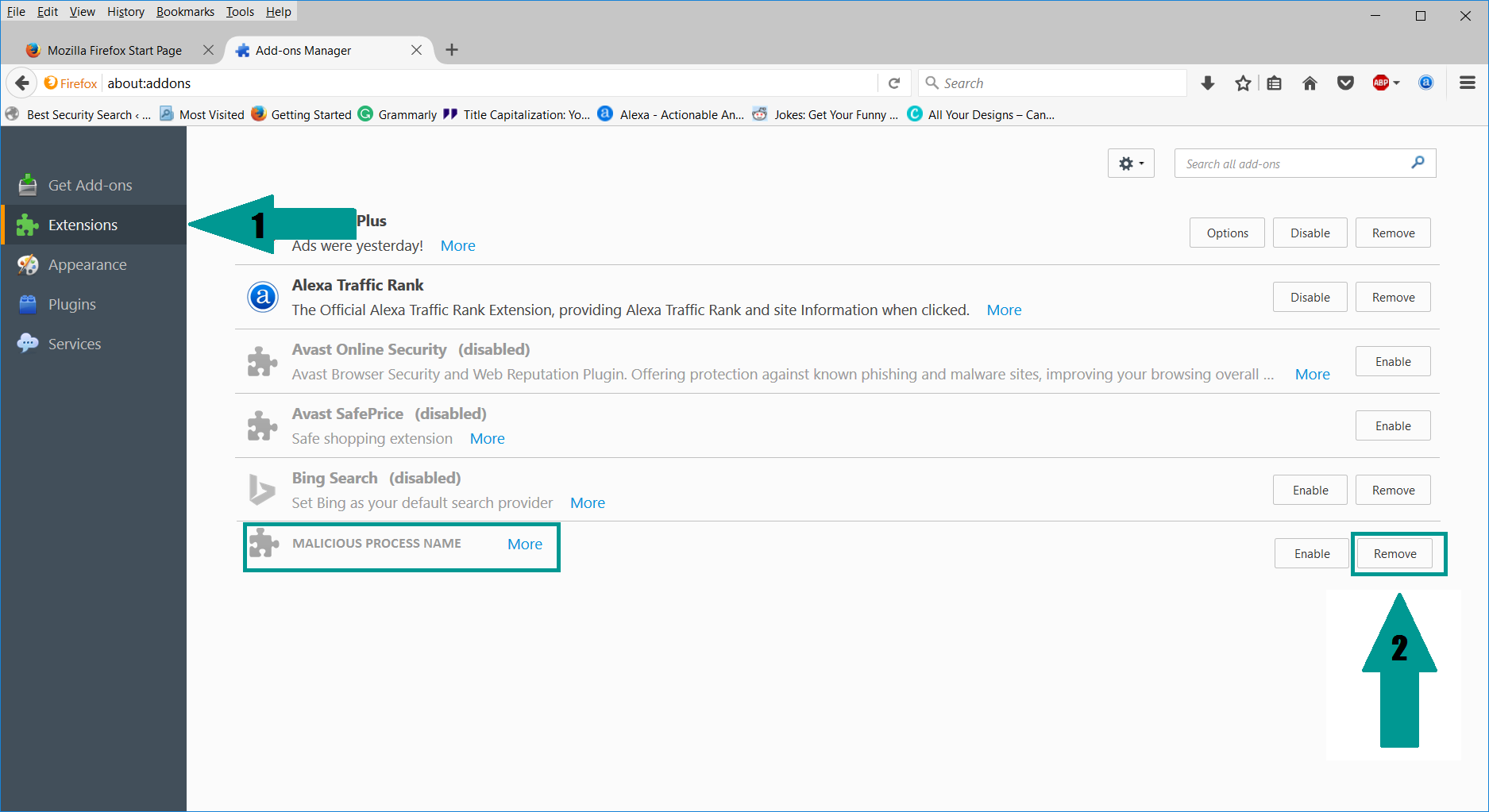
- 1) Start Mozilla Firefox. In the upper right corner, click on the Open menu icon and select “Add-ons“.

- 2) Inside the Add-ons Manager select “Extensions“. Search the list of extensions for suspicious entries. If you find any, select them and click “Remove“.
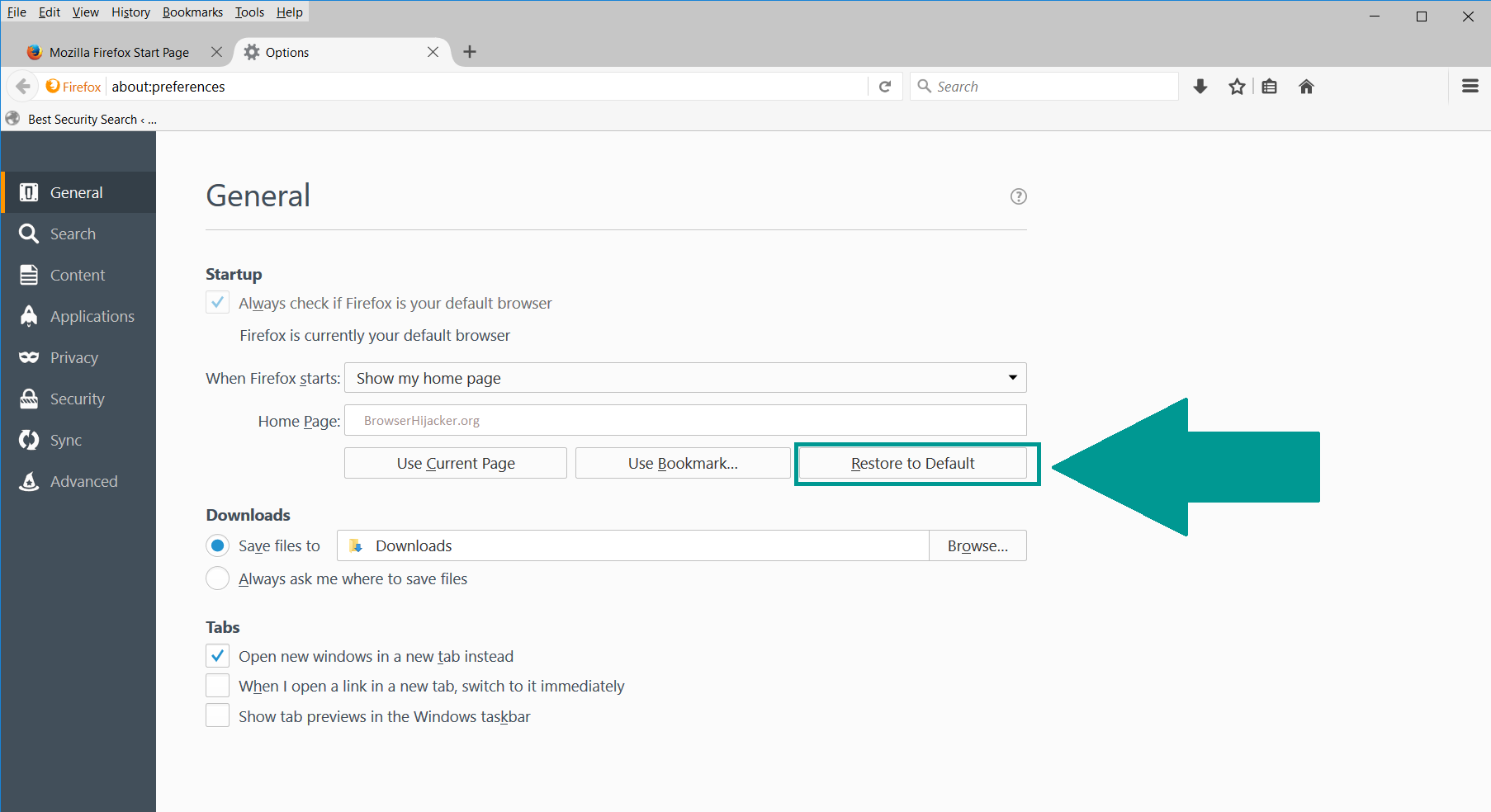
- 3) Click again on the Open menu icon, then click “Options“.

- 4) In the Options window, under “General” tab, click “Restore to Default“.
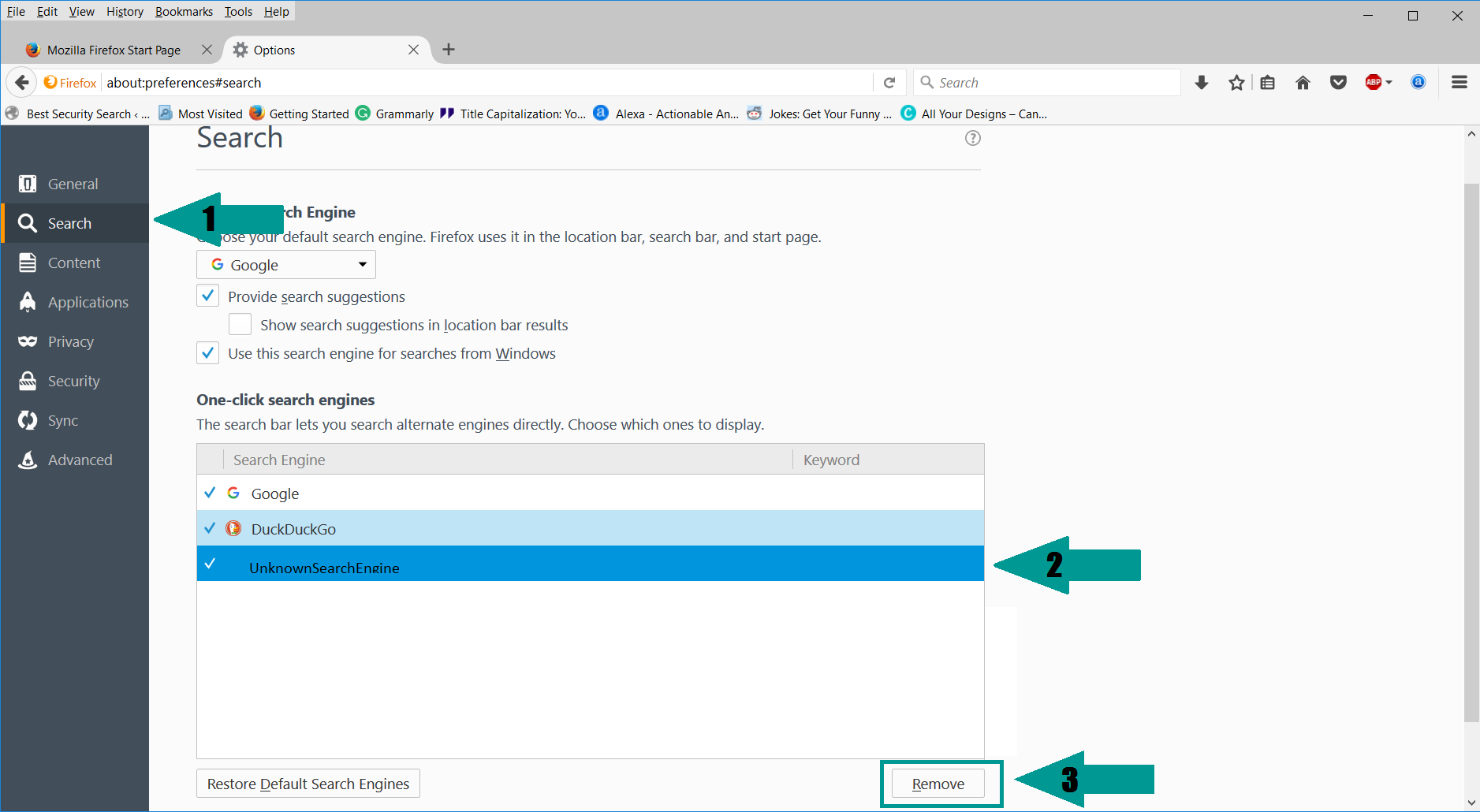
- 5) Select “Search” in the left menu, mark the unknown search engine and press “Remove”.
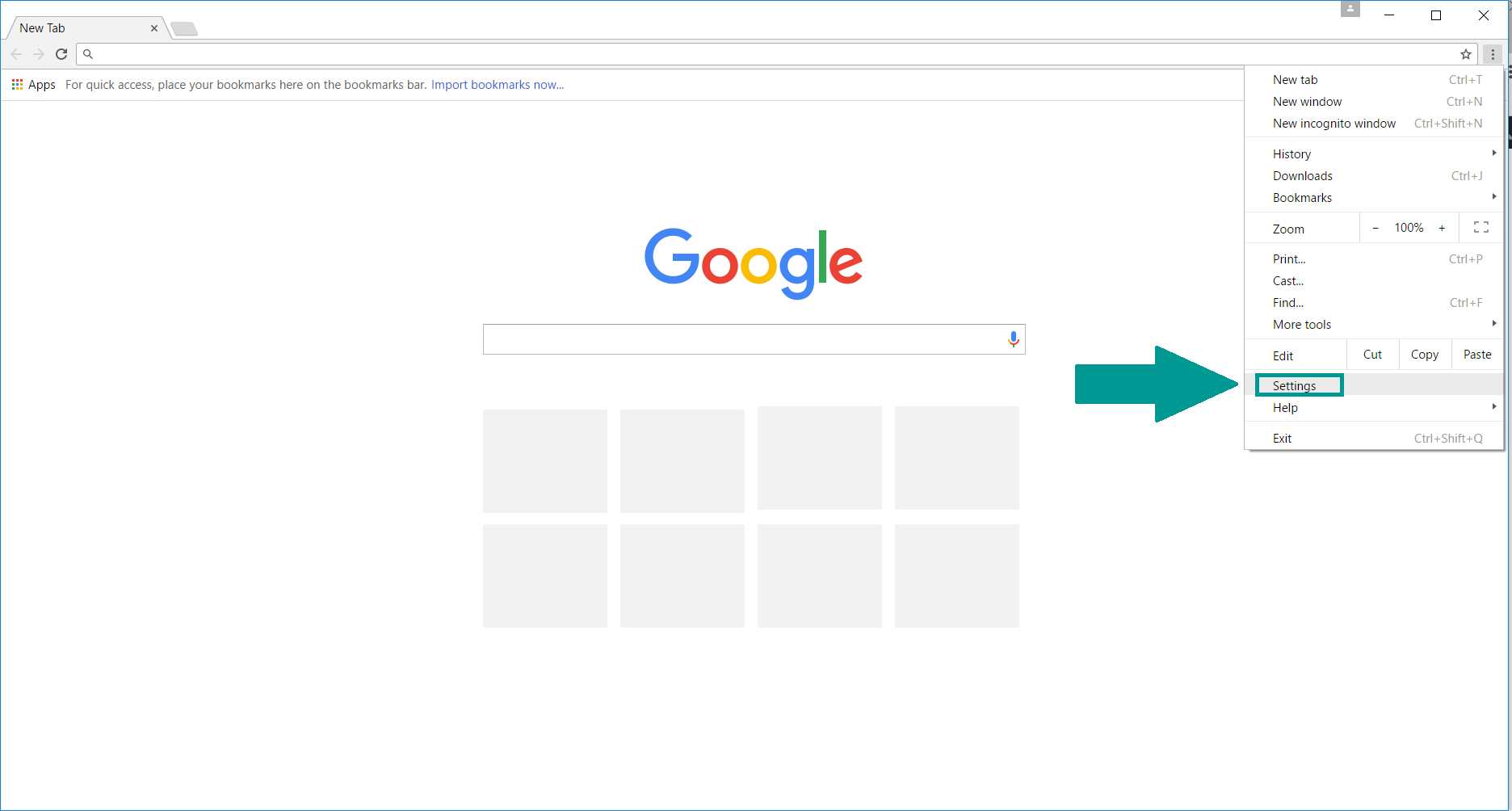
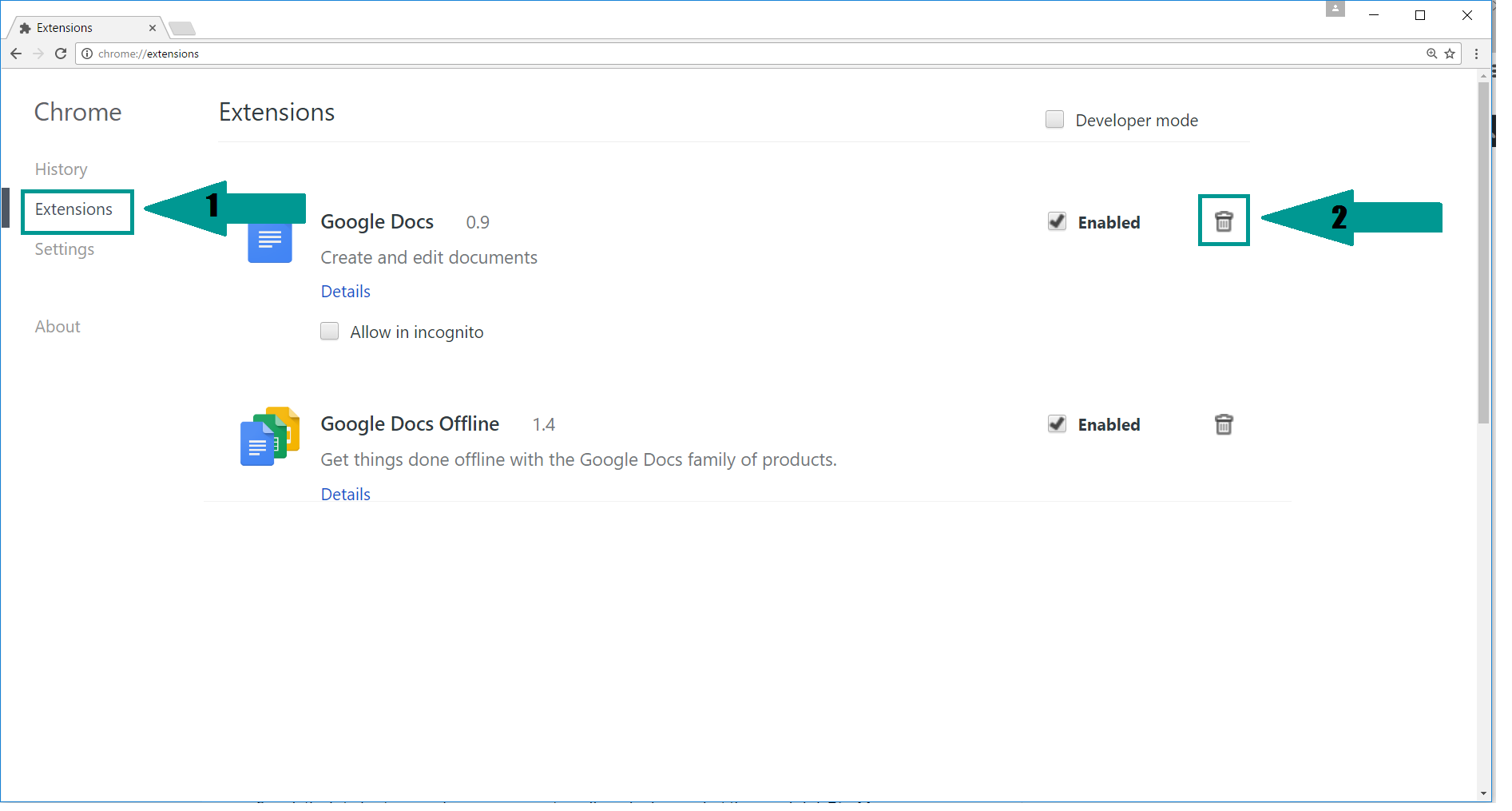
- 1) Start Google Chrome. On the upper-right corner, there a “Customize and Control” menu icon. Click on it, then click on “Settings“.
- 2) Click “Extensions” in the left menu. Then click on the trash bin icon to remove the suspicious extension.
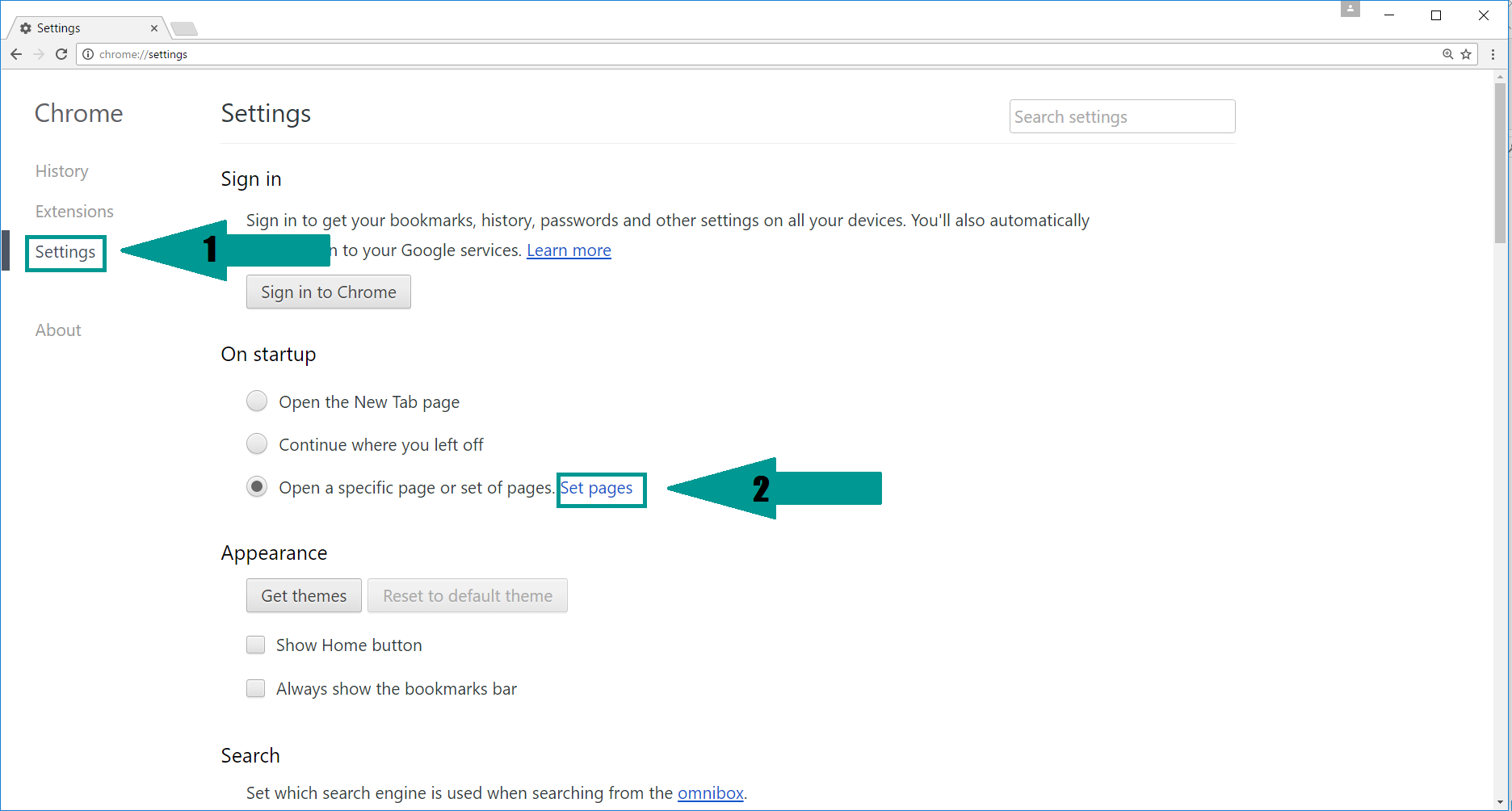
- 3) Again in the left menu, under Chrome, Click on “Settings“. Go under “On Startup” and set a new page.
- 4) Afterward, scroll down to “Search“, click on “Manage search engines“.
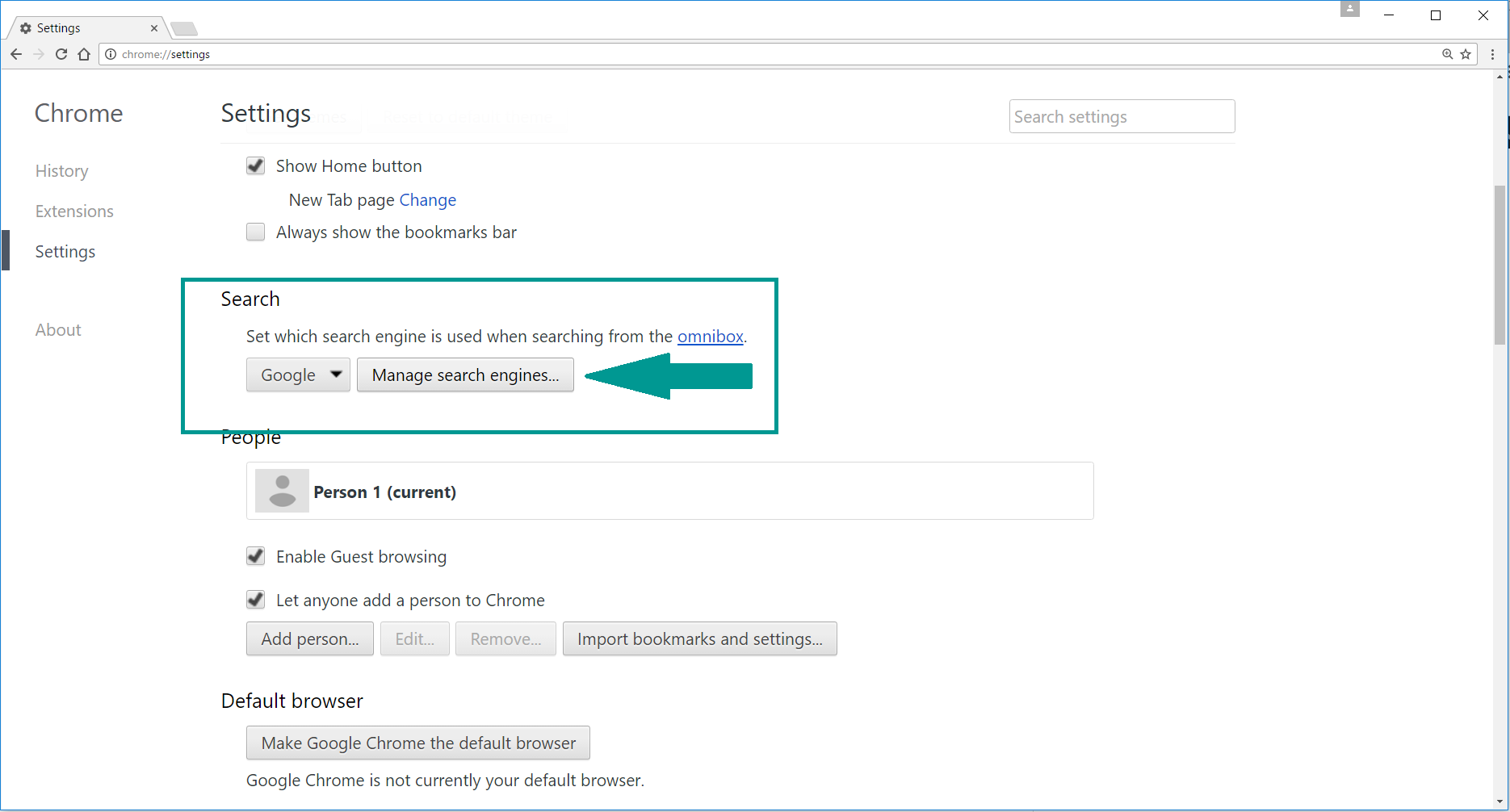
- 5) In the default search settings list, find the unknown search engine and click on “X“. Then select your search engine of choice and click “Make default“. When you are ready click “Done” button in the right bottom corner.
- 1) Start Internet Explorer. Go to the “Tools” menu and click on “Manage add-ons“.
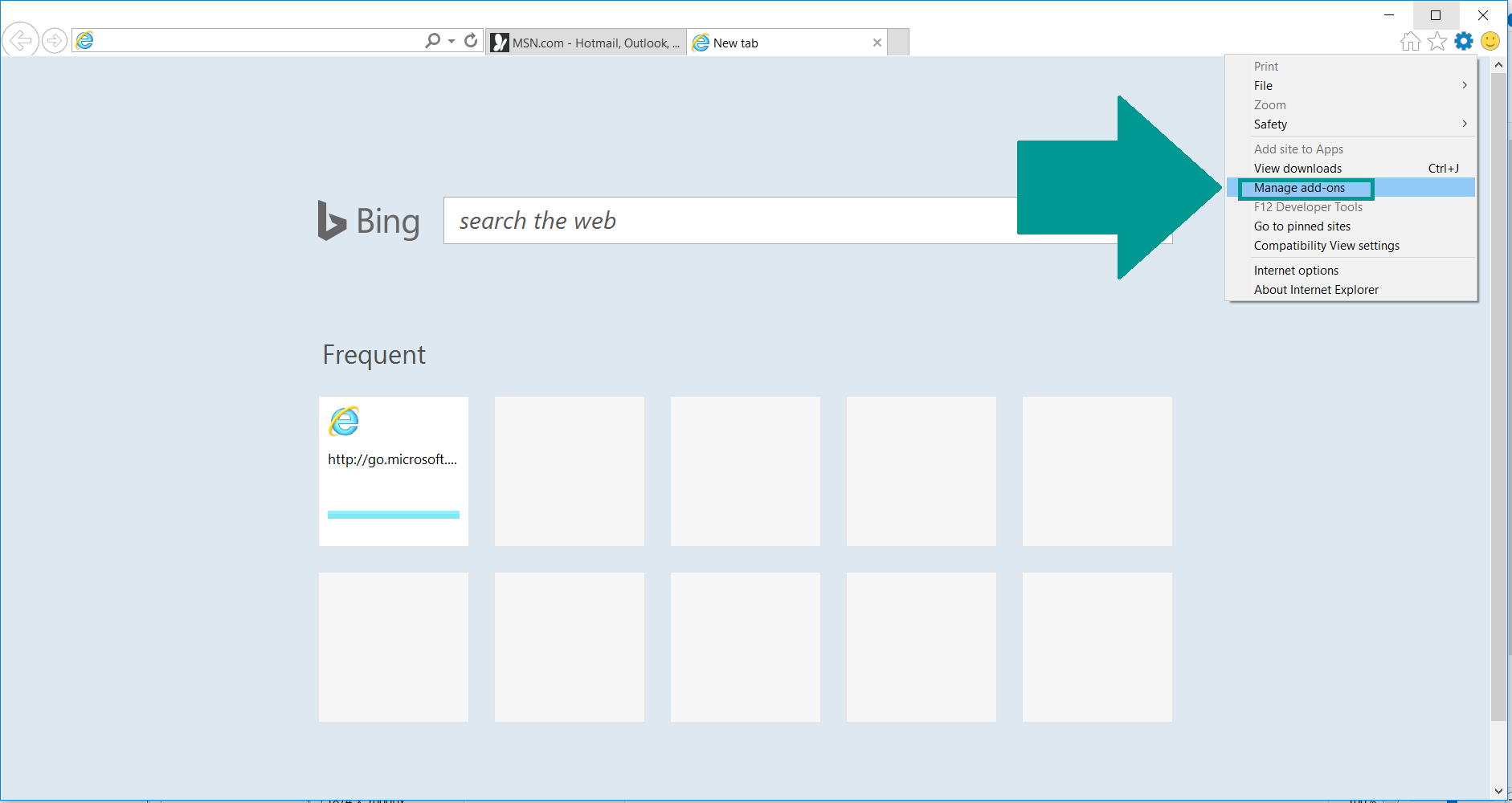
- 2) In the “Manage add-ons” window, bellow “Add-on Types“, select “Toolbars and Extensions“. If you see a suspicious toolbar, select it and click “Remove“.
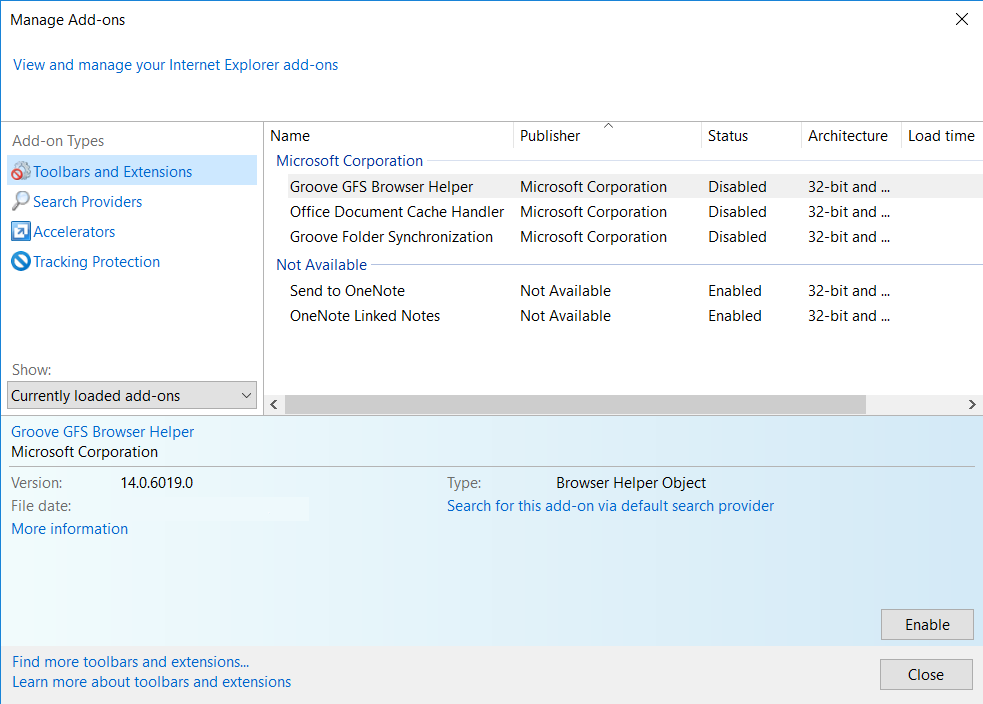
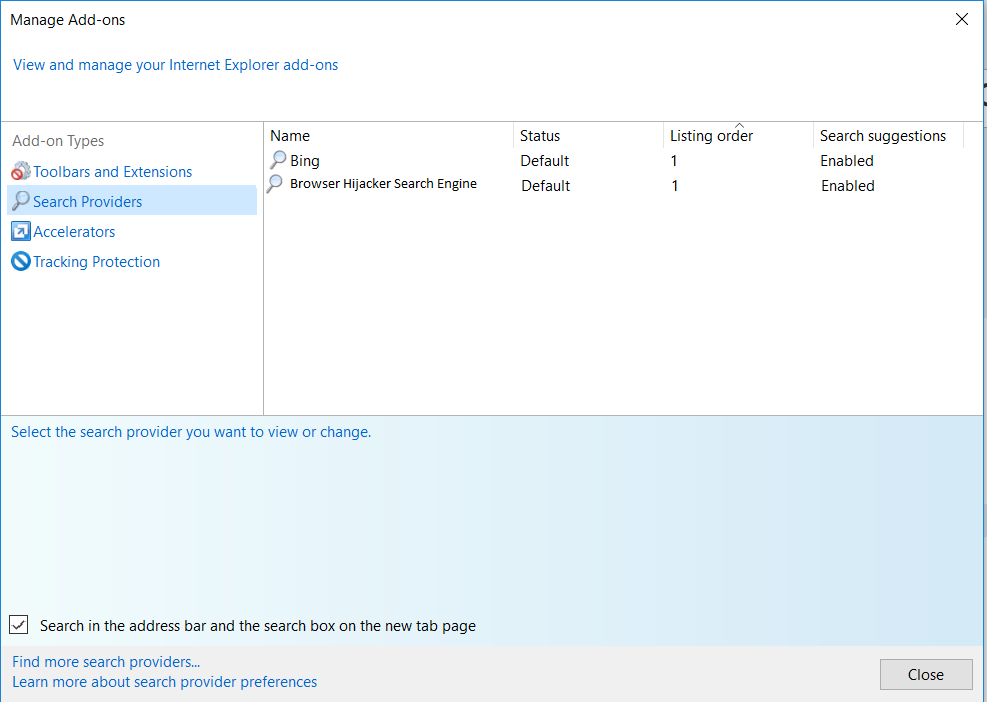
- 3) Then again in the “Manage Add-ons” window, in “Add-on Types“, Select “Search Providers“. Chose a search engine and click “Set as default“. Select the unknown search engine and click “Remove and Close”.
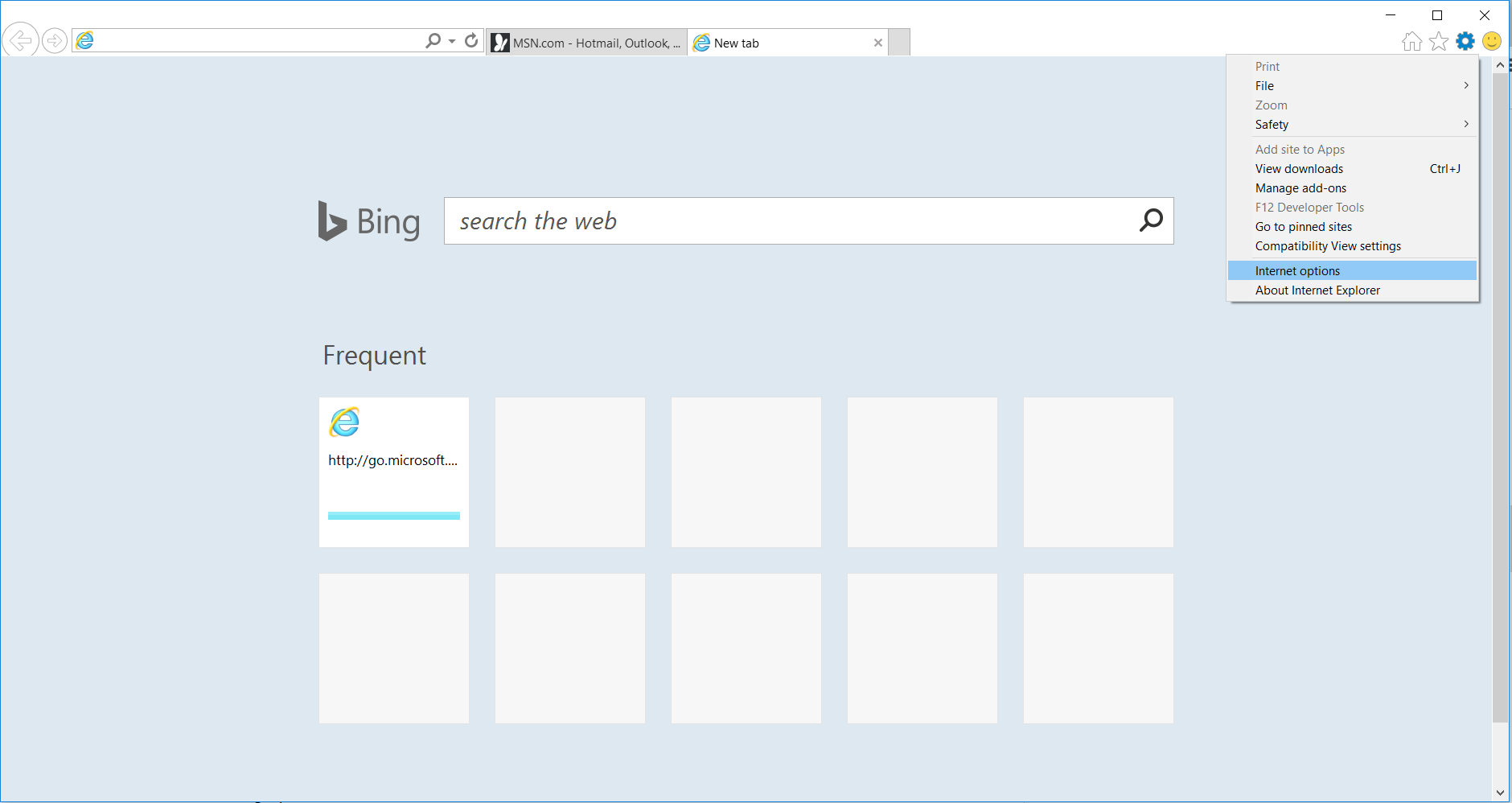
- 4) Open the Tools menu, select “Internet Options”.
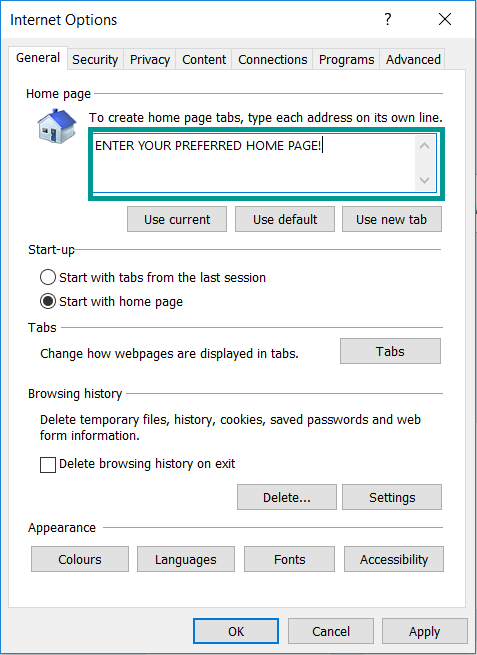
- 5) In the “General” tab, in “Home page”, enter your preferred page. Click “Apply” and “OK”.
STEP IV: Remove Completely Launchpage.org browser hijacker Browser Hijacker Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Preventive Security Measures
- 1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.



