This article contains instructions on how to remove .mole virus file from the infected computer and recover encrypted data.
The .Mole virus file is a typical ransomware infection that encrypts sensitive user data and appends the .mole extension to them. Then it demands a ransomware fee from the victims in an exchange for a decryption key. We strongly discourage victims to pay the ransom fee to the cyber criminals. Instead, remove the virus immediately and only then try to recover your lost data.
Manual Removal Guide
Recover .Mole Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
.Mole Virus File – Ransomware Features
July 2017 Update Recently a new strain of Mole ransomware has been detected. It is called Mole00-02 ransomware. All affected receive the .MOLE00 extension and are renamed using a built-in algorithm. A “_HELP_INSTRUCTION.TXT” file is crafted on various locations and serves as the ransomware note. Mole00-02 ransomware demands ransom of 1 Bitcoin from victims. Find out how to remove Mole00-02 ransomware virus and recover .MOLE00 files.
The infection of .mole virus file starts at the moment when a malicious executable file named plugin-office.exe or pluginoffice.exe is running on the computer. These files are designed to exploit unpatched vulnerabilities in the operating system and the installed apps. Once the ransomware’s payloads compromise the machine, it performs various system modifications like the creation of new registry entries and installation of further malicious files. In addition, it spawns a lot of processes. Unfortunately, the .mole virus doesn’t pass the vssadmin.exe process. By entering the commandline:
Vssadmin.exe delete shadows /all /quiet
.Mole virus deletes all saved shadow volume copies which are a form of backup and eliminates the possibility of file recovery via Shadow Explorer.
The ransomware has a built-in encryption module that employs RSA-1024 encryption to all target files. The corrupted files receive the malicious extension .mole and remain inaccessible until the unique private key generated during the encoding process is applied. As a result of .mole crypto virus contamination sensitive data like documents, text files, images, photos, music, projects, archives, videos, MS Office files, etc. are likely to be enciphered. The list of all file extensions encrypted by Mole ransomware virus includes:
.0 .1CD .1PA .1ST .2BP .36 .3DM .3DS .3FR .3GP .411 .4DB .4DL .4MP .73I .7Z
.8XI .A3D .AB4 .ABM .ABS .ABW .ACH .ACT .ADB .ADN .ADP .ADS .AES .AF2 .AF3 .AFS
.AFT .AFX .AGP .AHD .AI .AIC .AIF .AIM .AIT .AL .ALF .ANI .ANS .APD .APJ .APK
.APM .APS .APT .APX .ARC .ART .ARW .ASC .ASE .ASF .ASK .ASM .ASP .ASW .ASX .ASY
.ATY .AVI .AWP .AWT .AWW .AZZ .BAK .BAR .BAT .BAY .BBS .BC6 .BC7 .BD .BDB .BDP
.BDR .BGT .BIB .BIG .BIK .BKF .BKP .BM2 .BMP .BMX .BMZ .BNA .BND .BOC .BOK .BPW
.BRD .BRK .BRN .BRT .BSA .BSS .BTD .BTI .BTR .BYU .BZ2 .C .C4 .C4D .CAL .CAN
.CAS .CD5 .CDB .CDC .CDF .CDG .CDR .CDT .CDX .CE1 .CE2 .CER .CF .CFG .CFP .CFR
.CFU .CGM .CIN .CIT .CKP .CLS .CMA .CMD .CMT .CMX .CNM .CNT .CNV .CPC .CPD .CPG
.CPI .CPP .CPS .CPT .CPX .CR2 .CRD .CRT .CRW .CS .CSH .CSL .CSR .CSS .CSV .CSY
.CT .CV5 .CVG .CVI .CVS .CVX .CWT .CXF .CYI .DAC .DAD .DAF .DAS .DAT .DB .DB0
.DB2 .DB3 .DBA .DBC .DBF .DBK .DBR .DBS .DBT .DBV .DBX .DC2 .DCA .DCB .DCH .DCR
.DCS .DCT .DCX .DDD .DDL .DDS .DED .DER .DES .DF1 .DGC .DGN .DGS .DGT .DHS .DIB
.DIF .DIP .DIZ .DJV .DM3 .DMI .DMO .DMP .DNC .DNE .DNG .DOC .DOT .DP1 .DPP .DPX
.DQY .DRF .DRW .DRZ .DSK .DSN .DSV .DT .DT2 .DTA .DTD .DTW .DVI .DVL .DWG .DX
.DXB .DXF .DXG .DXL .EBD .ECO .ECW .ECX .EDB .EFD .EGC .EIO .EIP .EIT .EMD .EMF
.EML .EP .EPF .EPK .EPP .EPS .EQL .ERF .ERR .ESM .ETF .ETX .EUC .EXF .EXR .FAL
.FAQ .FAX .FB2 .FB3 .FBL .FBX .FCD .FCF .FDB .FDF .FDR .FDS .FDT .FDX .FES .FF
.FFD .FFF .FFT .FH .FH3 .FH4 .FH5 .FH6 .FH7 .FH8 .FHD .FIC .FID .FIF .FIG .FIL
.FIM .FLA .FLC .FLI .FLR .FLV .FM .FM5 .FMP .FMV .FOL .FOS .FP3 .FP4 .FP5 .FP7
.FPK .FPT .FPX .FRM .FRT .FSH .FT7 .FT8 .FT9 .FTN .FX0 .FX1 .FXC .FXG .FXR .FZB
.FZV .G3 .GDB .GEM .GEO .GFB .GGR .GHO .GIF .GIH .GIM .GIO .GPD .GPG .GPN .GRO
.GRS .GRW .GRY .GSD .GTP .GV .GWI .GZ .H .HBK .HDB .HDP .HDR .HHT .HIS .HKX
.HPG .HPI .HPL .HPP .HS .HTC .HWP .HZ .I3D .IB .IBD .ICN .IDC .IDX .IGT .IGX
.IHX .IIF .IIL .IIQ .IMD .INK .INT .IPF .IPX .ITL .ITM .ITW .IWD .IWI .J .J2C
.J2K .JAS .JB2 .JBR .JIA .JIS .JNG .JOE .JP1 .JP2 .JPE .JPG .JPS .JPX .JS .JTF
.JTX .JWL .JXR .K2P .KDB .KDC .KDI .KDK .KES .KEY .KF .KIC .KLG .KNT .KON .KPG
.KWD .LAY .LBF .LBM .LBT .LGB .LGC .LIS .LIT .LJP .LMK .LNT .LOG .LP2 .LRC .LRF
.LST .LTR .LTX .LUA .LUE .LUF .LVL .LWO .LWP .LWS .LYT .LYX .M .M2 .M3D .M3U
.M4A .M4V .MA .MAC .MAF .MAM .MAN .MAP .MAQ .MAR .MAT .MAW .MAX .MB .MBM .MCL
.MDB .MDC .MDE .MDF .MDN .MDT .ME .MEF .MFT .MFW .MIN .MKV .MLX .MML .MMW .MNG
.MNR .MNT .MOS .MOV .MP3 .MP4 .MPF .MPG .MPO .MPP .MRG .MRW .MSG .MSO .MT9 .MTE
.MUD .MWB .MWP .MX0 .MXL .MYD .MYI .MYL .NCF .NCR .NCT .ND .NDD .NDF .NEF .NFO
.NJX .NK2 .NLM .NOW .NRW .NS2 .NS3 .NS4 .NSD .NSF .NSG .NSH .NTL .NV2 .NWB .NX1
.NX2 .NYF .NZB .OBJ .OC3 .OC4 .OC5 .OCE .OCI .OCR .ODB .ODC .ODF .ODG .ODM .ODO
.ODP .ODS .ODT .OFL .OFT .OIL .OMF .ONE .OQY .ORA .ORF .ORT .ORX .OTA .OTG .OTH
.OTI .OTP .OTS .OTT .OVP .OVR .OWC .OWG .OYX .OZB .OZJ .OZT .P12 .P7B .P7C .P7S
.P96 .P97 .PAK .PAL .PAN .PAP .PAQ .PAS .PAT .PBM .PBO .PC1 .PC2 .PC3 .PCD .PCS
.PCT .PCX .PDB .PDD .PDF .PDM .PDN .PE4 .PEF .PEM .PFD .PFF .PFI .PFS .PFV .PFX
.PGF .PGM .PHM .PHP .PI1 .PI2 .PI3 .PIC .PIP .PIX .PJT .PL .PLC .PLT .PM .PMG
.PNG .PNI .PNM .PNZ .POP .POT .PP4 .PP5 .PPM .PPS .PPT .PRF .PRT .PRW .PS .PSD
.PSE .PSK .PSP .PST .PSW .PTG .PTH .PTX .PU .PUB .PUZ .PVJ .PVM .PVR .PWA .PWI
.PWR .PX .PXR .PY .PZ3 .PZA .PZP .PZS .QBA .QBI .QBO .QBP .QBR .QBT .QBW .QBY
.RB .RM .RNG .RPD .RPF .RPT .RRI .RS .RSB .RSD .RSR .RST .RT .RTD .RTF .RTP
.RTX .RUN .RW2 .RWL .RWZ .RZK .RZN .S3M .SAF .SAI .SAM .SAY .SB .SBF .SCC .SCH
.SCI .SCM .SCT .SCV .SCW .SD0 .SDA .SDB .SDF .SDM .SDW .SEP .SET .SFC .SFW .SGM
.SID .SIE .SIG .SIS .SK1 .SK2 .SKM .SLA .SLD .SLK .SLM .SLS .SMF .SMS .SNP .SNX
.SOB .SPA .SPE .SPH .SPJ .SPP .SPQ .SPR .SQB .SQL .SR2 .SRF .SRT .SRW .SSA .SSK
.ST .ST4 .ST5 .ST6 .ST7 .ST8 .STC .STD .STE .STI .STM .STN .STP .STR .STW .STX
.STY .SUB .SUM .SVA .SVF .SVG .SWF .SXC .SXD .SXG .SXI .SXM .SXW .T12 .T13 .T2B
.TAB .TAR .TAX .TB0 .TBN .TCX .TDF .TDT .TE .TEX .TFC .TG4 .TGA .TGZ .THM .THP
.TIF .TJP .TLB .TLC .TM .TM2 .TMD .TMP .TMV .TMX .TN .TNE .TOR .TPC .TPI .TRM
.TVJ .TXT .U3D .U3I .UDB .UFO .UFR .UGA .UNX .UOF .UOP .UOT .UPD .UPK .USR .V12
.V30 .VBR .VBS .VCF .VCT .VDA .VDB .VDF .VEC .VFF .VML .VNT .VOB .VPD .VPE .VPK
.VRP .VSD .VSM .VST .VSX .VTF .VTX .VUE .VW .W3X .WAV .WB1 .WB2 .WBC .WBD .WBK
.WBM .WBZ .WCF .WDB .WDP .WGZ .WKS .WLL .WMA .WMF .WMO .WMV .WN .WP .WP4 .WP5
.WP6 .WP7 .WPA .WPB .WPD .WPE .WPG .WPL .WPS .WPT .WPW .WRI .WSC .WSD .WSH .WTX
.WVL .X .X11 .X3D .X3F .XAR .XDB .XDL .XF .XLA .XLB .XLC .XLD .XLF .XLL .XLM
.XLR .XLS .XLT .XLW .XML .XPM .XPP .XPS .XSN .XWP .XXX .XY3 .XYP .XYW .Y .YAL
.YBK .YML .YSP .YUV .Z3D .ZDB .ZDC .ZIF .ZIP .ZW
The analyses of .mole virus samples reveal that it also creates new registry entries. To be more persistent the ransomware creates custom Windows registry values in the following sub-keys:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Modifications in these registry keys allow .mole virus to run its malicious executable files every time when Windows is started.
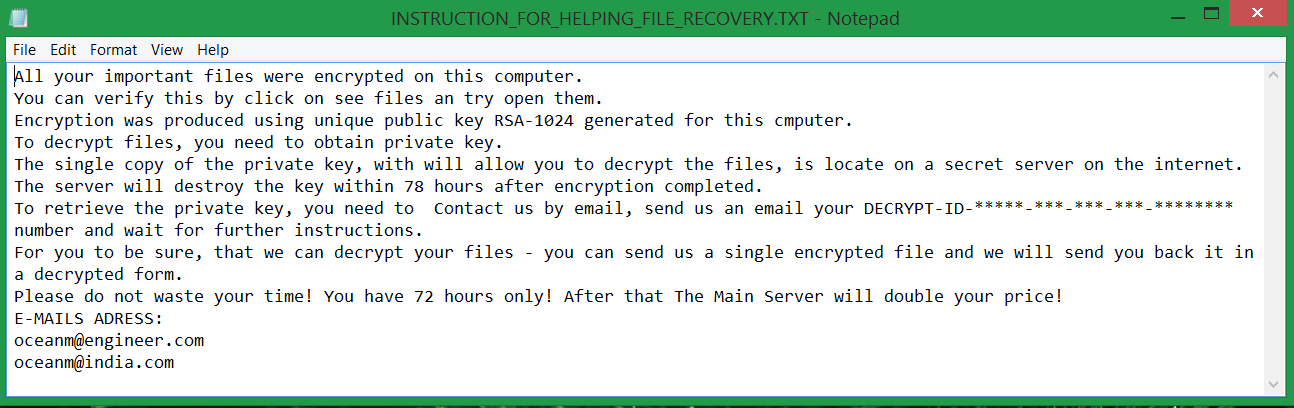
Victims will also notice a text file named INSTRUCTION_FOR_HELPING_FILE_RECOVERY.TXT dropped on their desktop and any directory with encrypted files. The file contains decryption instructions left by the crooks. The whole ransom note text reads:
All your important files were encrypted on this computer.
You can verify this by click on see files an try open them.
Encryption was produced using unique public key RSA-1024 generated for this cmputer.
To decrypt files, you need to obtain private key.
The single copy of the private key, with will allow you to decrypt the files, is locate on a secret server on the internet.
The server will destroy the key within 78 hours after encryption completed.
To retrieve the private key, you need to Contact us by email, send us an email your DECRYPT-ID-*****-***-***-***-******** number and wait for further instructions.
For you to be sure, that we can decrypt your files – you can send us a single encrypted file and we will send you back it in a decrypted form.
Please do not waste your time! You have 72 hours only! After that The Main Server will double your price!
E-MAILS ADRESS:
[email protected]
[email protected]
Cyber criminals are trying to urge victims into sending an email with the unique decrypt ID to [email protected] or [email protected] and wait for further instructions. The typical scenario includes the distortion of a ransom in BTC transferred to a predefined address. Once this happens, they probably will deliver the decryption key. For the sake of their security, we advise all victims of .mole ransomware to avoid any negotiations with the crooks. The instructions below serve as a step-by-step guide through the .mole virus removal process. When the threat is in the past .mole files can be retrieved by the freely available decryption tool developed by CERT-PL. Find it at the instructions below.
Distribution Techniques of .Mole Virus File
Mole virus file payloads are primarily distributed via spam email campaigns that may be disseminated worldwide. The email subject line, sender, text message, and provided links or attachments may be different for every single email.
A recent report made by the malware analysist Brad Duncan reveals picky details about .mole virus file distribution. Many malspam campaigns that push the ransomware were impersonating the United States Postal Service (USPS). Most of them inform about a delivery problem and point out a link to follow. It is supposed that the link will provide additional information on the case, however, it lands on fake Microsoft Office portal pages with Google Docs URLs hidden in a button. The button is following a text that states:
“This document cannot be read in your browser.
Download and install the latest plugin version.”
A click on the button initiates the download of an executable file from a Google Doc URL. Actually, the .mole ransomware virus is disguised as an Office plugin, and the infection process starts once it lands on the computer. The detected and analyzed executable files that trigger the .mole ransomware infection are named plugin-office.exe and pluginoffice.exe.
As other ways of .mole ransomware distribution may be used messages and posts on social networks and freeware bundling practices. So beware, the .mole virus file may be stalking you.
Spicy news:
Could you recognize the threat?
Our team has received an email from a user who is using the [email protected] address. The email impersonates the “USPS Ground Support” and the subject line reads – “Official letter from USPS support team”. The sender is trying to convince us that we have ordered a product that wasn’t delivered to our address. However, this it is certainly not true, and the aim of this email is to trick us into following a link provided in the message.
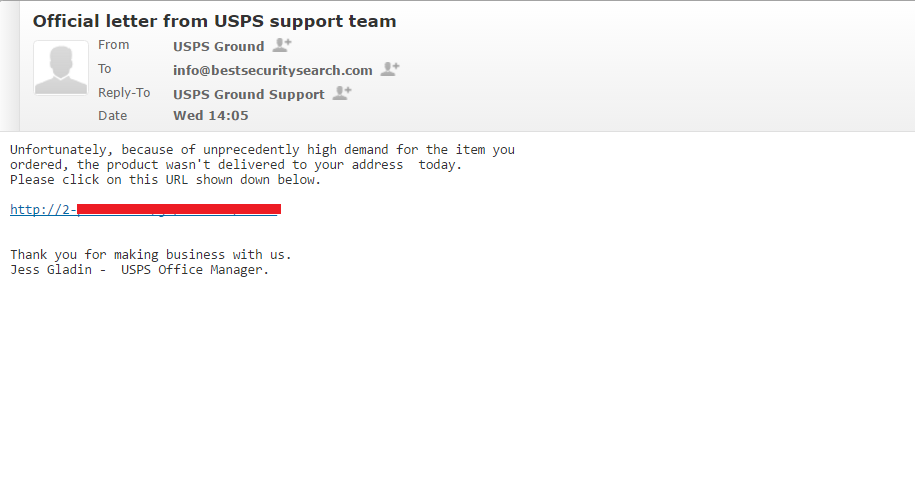
It was more than obvious that we had received a spam email that is distributing a corrupted link that is likely to install malware on the PC if entered. Furthermore, we know that the .mole ransomware propagators impersonated the USPS services in several of their attack campaigns. So, we have recognized the scam and prevent an eventual infection with ransomware. By sharing our experience, we hope that it will be easier for our readers to recognize the threat. Being informed is a sure way to stay a step ahead of the malware.
.Mole Virus File Mass Email Spam Campaign Details
Another source of .Mole virus file infections is an attack campaign coordinated with the help of the Rig Exploit kit. The hackers use the EITEST campaign to deliver template emails that carry the virus. Captured samples of the .mole ransomware virus indicate that the criminals have used a hacked site (1tajrobe.com) and two additional components – a RIG exploit kit landing page and a Mole-specific ransomware check-in page. The used emails are generic and hosted on freely available services. This likely means that they are probably used as relays – [email protected] and [email protected].
Another email spam campaign is associated with counterfeit USPS delivery reports and other information that is commonly used by the service. The hackers utilize several templates. The messages are generated automatically and follow a predefined model:
- The hackers send out links that lead to a malicious site.
- The site automatically redirects to to another domain where a counterfeit Word Online site is displayed to the victims.
- A ZIP archive is generated and downloaded to the victim computer.
- The zip archive contains a malicious script which installs the .Mole virus payload.
A key characteristic of the spread campaign is that it uses a redirection domain (servivedelivery.com) that may look legitimate to some users. The links from the emails total 30 different domains and 2 separate counterfeit Word Online instances. There are several partial URLs that the malware researchers were able to extract that use the country codes of Poland (pl), Belgium (be) and Romania (ro). They are used for deploying additional malware to the targets.
August 2017 Update: New Variants Active
During the past few months security analysts captured several strains that are descendant from the .mole file virus. They are sourced from the original code and now form a loose family of related threats. Fortunately the threats have not been able to cause large-scale infections.
Variants include Mole00-02 ransomware and MOLE03 ransomware.
Remove Mole Virus and Restore Encrypted Files
WARNING! Manual removal of the Mole ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Mole Virus File – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .Mole Files
WARNING! All files and objects associated with Mole ransomware virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD .Mole Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
UPDATE: Security researchers that are part of the “No More Ransom” project have updated their decryption tool list with a Mole Decryptor. The thorough reverse-engineering process of Mole ransomware samples performed by specialists at CERT Polska team “turned out to be a good idea”, they said. Now victims of Mole ransomware virus can retrieve the encrypted data without having to pay the criminals. Find out how to restore .mole files by visiting the No More Ransom page with decryption tools.
In case that some files remain corrupted after the decryption process you can try alternative data recovery solutions.
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



