Reyptson is the name given to a ransomware that encrypts sensitive files and locks PC screen with a crafted message. In a case of infection Reytpson ransomware virus appends a file extension of the same name to all corrupted files and limits the access to them. Then it drops a ransom message file to instruct victims how to pay the ransom and decrypt .REYPTSON files. This article aims to help victims with Reyptson ransomware removal and .REYPTSON data recovery.
Manual Removal Guide
Recover .REYPTSON Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Reyptson Ransomware – Dissemination Details
At this point, it seems that Reyptson Ransomware attacks Spanish-speaking users. However, it is likely that its authors will spread it globally soon. Reyptson Ransomware attack campaigns are likely to distribute its payloads via spam emails. That emails usually pose as legitimate services or even acquaintances attempting to trick users into interacting with an attached file or clicking a deceptive link. File attachments that disseminate ransomware infections are crafted by hackers. They may be PDF files that contain malicious JavaScript code, documents with malicious macros, and other files that contain code that can exploit system vulnerabilities once it is opened on the PC. Deceptive links, on the other hand, may redirect you to a web page that will unnoticeably download Reyptson payloads on the system.
One of the first attack campaigns of Reyptson Ransomware follows the stream:
- 1. A crafted email delivers fake details about an invoice and provides a download button for the invoice.
2. Once the button is clicked, a RAR file is downloaded on the PC.
3. The RAR contains the malicious Reyptson Ransomware payload so after it is opened the infection process is triggered as well.
4. While Reyptson Ransomware is encrypting data it distracts user’s attention by displaying a fake PDF document with a Windows notification window pop up. The pop up states that the PDF file could not be opened because its file type is not supported or it is corrupted.
5. Upon infection, Reyptson ransomware collects SMTP (Simple Mail Transfer Protocol) credentials and sends the same fake invoice email to every Thunderbird contact. So it is self-replicating via email and acts like a worm which makes it a very dangerous threat.
Read Also: Microsoft Warning Alert Pop-up Virus
Reyptson Ransomware Virus – Infection Flow
First, Reyptson crypto virus executes a malicious file Reyptson.exe that is designed to initiate the infection flow. In order to carry out successful infection, the ransomware drops several other malicious files. That files are situated in the following Windows folders:
%APPDATA%
%LOCALAPPDATA%
%TEMP%
Data encryption is the top priority of Reyptson ransomware virus. The threat uses AES-128 cipher algorithm to modify the original code of target files. Afterward, it renames them and appends the malicious extension .REYPTSON at the end of the name.
The threat targets documents such as PDFs, text files, docs, and other files frequently used files that contain valuable information – images, videos, music, projects, archives, databases, etc. Eventually, only JPG files, as well as all essential system files, are likely to remain untouched by Reyptson ransomware.
Some of the malicious files associated with Reyptson ransomware virus are designed to modify Windows registry entries. Modifications of certain key values allow the ransomware to lower internet security settings, display its ransom note on the PC screen and set up automatic execution of malicious once the Windows is started.
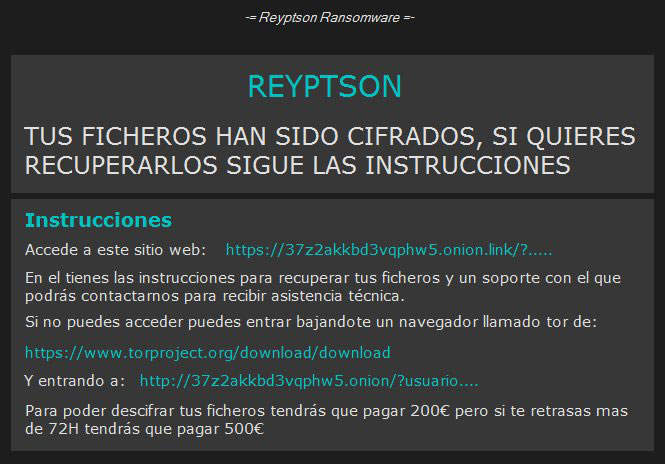
By adding specific values to the registry key, HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Reyptson opens a pop-up window on the PC screen. The Reyptson Ransomware pop up cannot be closed as long as the infection is running on the computer. All it reads is written in Spanish:
REYPTSON
TUS FICHEROS HAN SIDO CIFRADOS, SI QUIERES RECUPERARLOS SIGUE LAS INSTRUCCIONES
Instrucciones
Accede a este sitio web: xxxxs://37z2akkbd3vqphw5.onion.link/?…..
En el tienes las instrucciones para recuperar tus ficheros y un soporte con el que
podrás contactarnos para recibir asistencia técnica.
Si no puedes acceder puedes entrar bajandote un navegador llamado tor de:
https://www.torproject.org/download/download
Y entrando a: xxxx://37z2akkbd3vqphw5.omon/7usuario….
Para poder descifrar tus ficheros tendrás que pagar 200€ pero si te retrasas mas
de 72H tendrás que pagar 500€
With the help of translation service it becomes clear that what is said on Reyptson Ransomware pop up in English reads:
REYPTSON
YOUR FILES HAVE BEEN CIRCULATED, IF YOU WANT TO RECOVER THEM FOLLOW THE INSTRUCTIONS
Instructions
Access this website: xxxxs: //37z2akkbd3vqphw5.onion.link/? …..
In it you have the instructions to recover your files and a support with which
You can contact us for technical assistance.
If you can not log in you can enter a browser called tor from:
Https://www.torproject.org/download/download
And entering: xxxx: //37z2akkbd3vqphw5.omon/7user ….
In order to decrypt your files you will have to pay 200 € but if you delay more
From 72H you will have to pay € 500
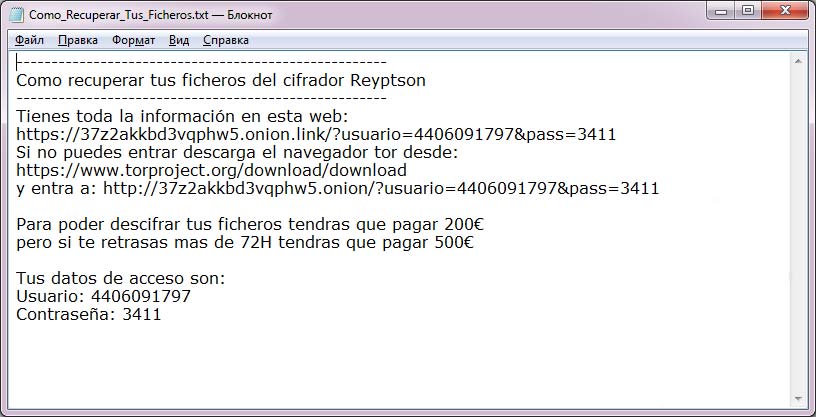
In another text file Como_Recuperar_Tus_Ficheros.txt dropped by Reyptson ransomware hackers leave second ransom message again in Spanish:
Como recuperar tus ficheros del cifrador Reyptson
—
Tienes toda la información en esta web:
xxxxs://37z2akkbd3vqphw5.onion.link/?usuario=4406091797&pass=3411
Si no puedes entrar descarga el navegador tor desde:
xxxxs://www.torproject.org/download/download
y entra a: xxxx://37z2akkbd3vqphw5.onion/?usuario=4406091797&pass=3411
Para poder descifrar tus ficheros tendras que pagar 200€
pero si te retrasas mas de 72H tendras que pagar 500€
Tus datos de acceso son:
Usuario: 4406091797
Contraseña: 3411
Its English version reads:
How to recover your files from the Reyptson cipher
—
You have all the information in this web:
Xxxxs: //37z2akkbd3vqphw5.onion.link/? Username = 4406091797 & pass = 3411
If you can not log in, download the tor browser from:
Xxxxs: //www.torproject.org/download/download
And go to: xxxx: //37z2akkbd3vqphw5.onion/? User = 4406091797 & pass = 3411
In order to decrypt your files you will have to pay € 200
But if you delay more than 72H you will have to pay € 500
Your login details are:
User: 4406091797
Password: 3411
Reyptson drops the second ransom message in each folder that contains encrypted file. And as it becomes clear hackers demand € 200 ransom until the dead line of 72 hours expires when the ransom increase up to € 500. Tor web addresses provided by hackers are currently active:
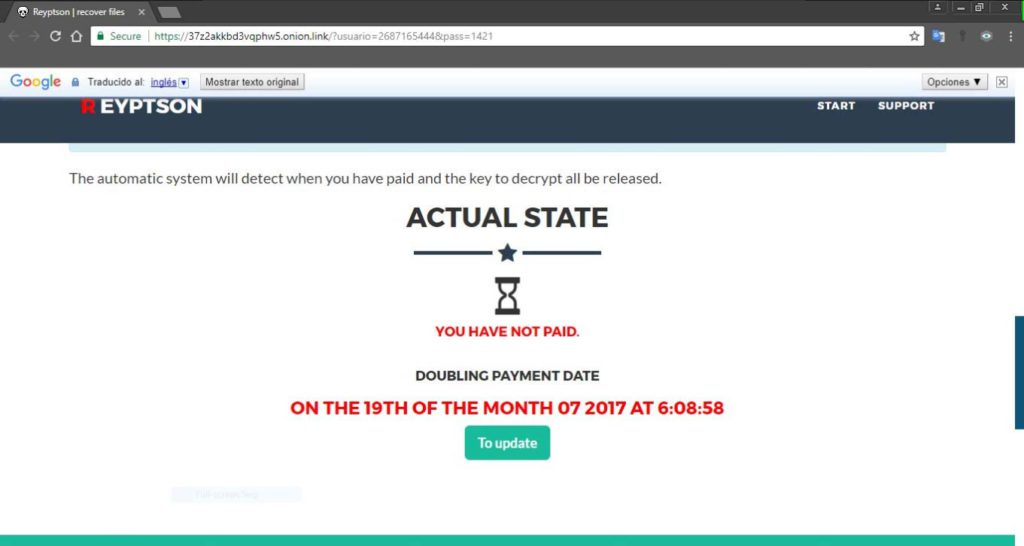
No matter what the sum is, it is always better to avoid ransom payment before you try to cope with the problem by yourself or with the help of security specialist.
The good news is that as it appears Reyptson ransomware does not delete Shadow Volume Copies. Thus .REYPTSON files may be recovered by using System Restore Point. All .REYPTSON data recovery steps via this method can be found in the removal instructions below. If some files remain encrypted after the process you may try to recover .REYPTSON files via the other suggested alternative methods.
Remove Reyptson Ransomware Virus and Restore Data
WARNING! Manual removal of Reyptson Ransomware Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Reyptson Ransomware Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .REYPTSON Files
WARNING! All files and objects associated with Reyptson ransomware should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD Malki Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



