Computer security researchers have developed an open-source Python-based backdoor which uses the Telegram service for C&C servers.
The BrainDamage Backdoor Employs Telegram For C&C Servers
A team of programmers have created a dangerous computer backdoor which is written in the Python programming language known as Brain Damage. The dangerous characteristic about it is that it is a fully-featured malware that uses the Telegram API to control and relay the remote C&C servers. Malicious users can use to launch dangerous attacks against predefined targets. The backdoor is organized around the use of the Telegram Messenger. Its use is done through a bot which is controlled by an API token. Using a Gmail (Google) account malicious users can control it. When the backdoor is launched at first the following actions are executed:
The necessary files are copied to the startup path and relevant registry entries are done. The hackers have devised a warning prompt which displays an error notification. This is done to fool the users that the malicious file is broken.
In the meantime the dangerous code is placed in a hidden folder.
When the initialization process is complete the malware opens up a network connection and starts to listen for any remote commands that are relayed by the servers.
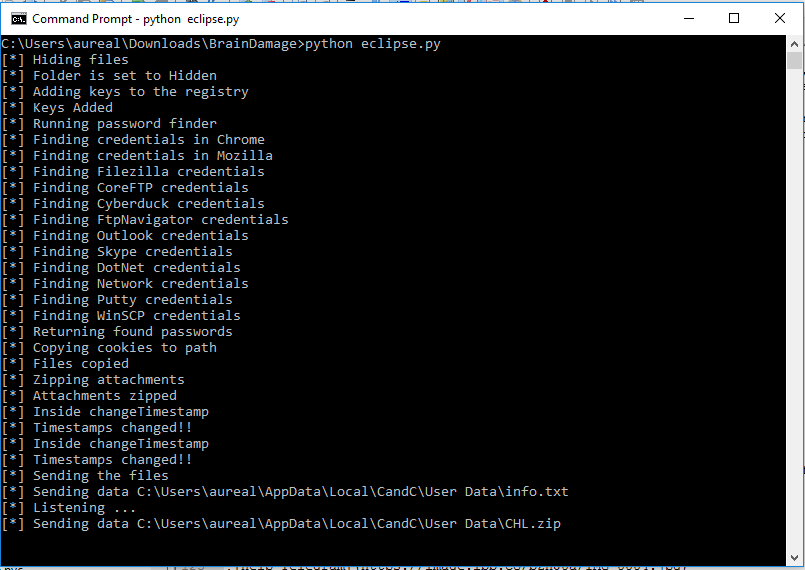
The BrainDamage backdoor has many advanced features that allows it to be used as an efficient payload downloader and a remote access and spying Trojan. Once installed on the target system it can attain Persistence, making it difficult to remove via manual means. This is done by modifying key Windows settings and placing relevant registry key values and boot entries. What’s more dangerous is that the virus can spread to removable devices via USB and it can launch attacks against other network devices. Its developers have bundled a port scanner which is able to lookup any running services of machines and devices running in the internal network of the compromised hosts. The full list of features includes the following modules:
Spying On The Victims – The backdoor can capture screenshots at will. In addition the included keylogger is able to capture all keystrokes that are placed by the user. This makes the virus capable of harvesting all kinds of private information and accounts. When a microphone is available the virus can also capture live audio which allows it to be used as an eavesdropping device as well. When configured properly it can also harvest cookies, history and accounts from the installed web browsers.
Account Credentials Harvesting – The backdoor is able to extract information about the usernames and passwords of popular applications. The list includes instant messenger apps, FTP clients, web browsers, network credentials and email software.
Sabotage – BrainDamage is able to rename target files and archive them acting as a rudimentary ransomware. More complete features can be implemented if the developers customize it further or add a true ransomware payload in the infection process.
System Modification – The hackers can opt to change the wallpaper (displaying a message to the victims), modify application settings, disable functionality or execute other malicious activity at will. Execution of remote arbitrary commands is a core feature.
System Information Harvesting – The backdoor can actively gather information about the compromised system such as the operating system version, internal IP address, installed drivers and associated hardware and etc.
The bot itself comes with an extensive list of commands that can be used by the hackers to execute various actions on the infected machines:
whoisonline – Lists the currently active bots.
destroy – Removes the infection and cleans up its traces.
#cmd – Executes arbitrary commands using the Windows Command Prompt.
#download – Downloads a file from a remote address.
#execute – Launches a power event (Shutdown, Restart, Logoff or Lock).
#screenshot – Takes a screenshot.
#send – Sends the harvested passwords, list of connected drives, keystrokes and open applications list.
#set – Configures the output file.
#start – Starts a malicious action such as keylogger or the audio recording.
#stop – Stops the malicious action.
#wallpaper – Changes the users wallpaper.
#find – Launches the port scanner.
#help – Launches a brief help file.
The utility is named after the famous song by Pink Floyd from the Dark Side Of The Moon album. Computer users can protect themselves from the backdoor and other similar threats by using a quality anti-malware solution. For more information click here.



