The ThunderCrypt ransomware virus is a dangerous threat that encrypts user files with a strong cipher. When a system is infected it shows a ransomware note that extorts the victims to pay a ransomware fee in the Bitcoin digital currency. The amount equals 600 US Dollars. Users can remove the virus by:
DOWNLOAD ThunderCrypt virus removal tool.
You can then follow the steps below to restore your files.
How Can ThunderCrypt Virus Infiltrate the PC?
ThunderCrypt ransomware virus is delivered to the victims mainly by posing as a counterfeit Adobe Flash Player update. The security researchers uncovered that several samples have been found on posts located on Thai internet forums. Other methods of distribution include the following:
- Email Spam Messages – The hackers behind the ThunderCrypt ransomware virus can create and coordinate large-scale email spam campaigns based on predefined templates. The virus binary may be directly attached to messages that pose as being sent by a legitimate user, company or government institution. In other cases it can be linked to a hacker-controlled site.
- Hacker-controlled Sites – The criminals can opt to distribute the dangerous ThunderCrypt ransomware virus via fake download portals. P2P networks like BitTorrent can also be used to spread the malware.
- Dangerous Scripts and Ad Networks – Hacker-controlled scripts inserted on web sites and dangerous ad networks can lead to a ThunderCrypt ransomware virus infection.
- Browser Hijackers – The dangerous browser extensions also known as browser hijackers can deliver the ThunderCrypt ransomware virus to target machines. In addition they endanger the victims privacy by harvesting stored data such as: stored cookies, account credentials, form data, bookmarks, history and etc. They effectively change important browser settings like the default home page, search engine and new tabs page. Usually the hijackers are made for the most popular web browsers:Mozilla Firefox, Google Chrome, Mozilla Firefox, Internet Explorer and Microsoft Edge.
- Payload Delivery – Another threat may drop the ThunderCrypt ransomware virus as instructed.
ThunderCrypt Virus – Ransomware Features
The ThunderCrypt ransomware virus is a newly detected malware which uses a dangerous encryption engine upon infection. The threat uses a combination of the AES and RSA ciphers. Like other similar malware the Thundercrypt ransomware virus uses a built-in predefined list of file type extensions. Depending on the issued attack campaigns the criminals can customize the target extensions. In its current form the samples process the most commonly used user data: music, photos, videos, archives, backups, databases, configuration files and etc.
All processed data is renamed using a hacker-supplied extensions. When this process is complete the Thundercrypt ransomware virus message is displayed using a malicious lockscreen, it effectively prevents ordinary user interaction.
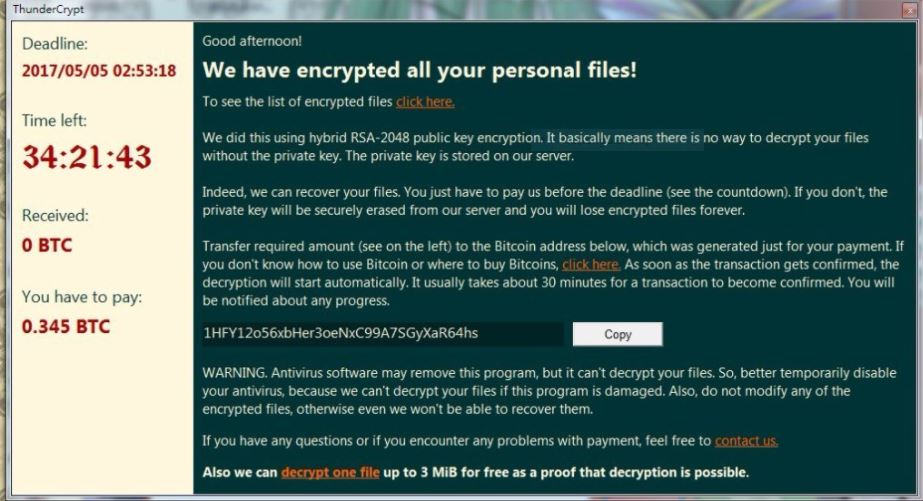
The following message is shown to the victims:
Good afternoon!
We have encrypted all your personal files!
To see the list of encrypted files click here.
We did this using hybrid RSA-2048 public key encryption. It basically means there is no way to decrypt your files without the private key. The private key is stored on our server.
Indeed, we can recover your files. You just have to pay us before the deadline (see the countdown). If you don’t the private key will be securely erased from our server and you will lose encrypted files forever.
Transfer required amount (see on the left) to the Bitcoin address below, which was generated just for your payment. If you don’t know how to use Bitcoin or where to buy Bitcoins, click here. As soon as the transaction gets confirmed, the decryption will start automatically. It usually takes about 30 minutes for a transaction to become confirmed. You will be notified about any progress.
1HFY12o56xbHer3oeNxC99A7SGyXaR64hs [Copy] WARNING. Antivirus software may remove this program, but it can’t decrypt your files. So, better temporarily disable your antivirus, because we can’t decrypt your files if this program is damaged. Also, do not modify any of the encrypted files, otherwise even we won’t be able to recover them.
If you have any questions or if you encounter any problems with payment, feel free to contact us.
Also we can decrypt one file up to 3 MiB for free as a proof that decryption is possible.
Using this information we can conclude the following about the ThunderCrypt ransomware virus:
- The ThunderCrypt ransomware virus creates a list of all processed data which can be used to inspect the committed damage.
- The hackers behind the ThunderCrypt ransomware virus have stated that they are using a hybrid encryption method using the RSA-2048 cipher. This is a strong method which is able to be overcome using the pair private key or a quality anti-malware solution.
- Like other similar viruses this one also uses a time limit to further extort the victims into paying the ransomware fee.
- The captured samples indicate a request sum of 0.345 Bitcoins which is the equivalent of about 605 US Dollars.
- The scripts included in the ThunderCrypt ransomware virus creates an unique Bitcoin address for each infected host. This severely limits the malware researchers from discovering the scale of the attack campaigns.
- ThunderCrypt ransomware virus warns the victims that the use of anti-virus software may interrupt the process or cause harm to the computers. This is an attempt to deceive the computer users from removing the threat.
- The hackers behind the ThunderCrypt ransomware virus include a support option in case the victims want to contact them.
This virus is similar to other basic ransomware types such as the clouded ransomware.
ThunderCrypt Ransomware Virus Removal
Once you’re done with the removal process, there are some alternative data recovery solutions may help to restore sensitive user files. OK, let’s begin..
Ransomware Removal Steps
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
- 1) Open My Computer/This PC
2) Windows 7
- – Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
- – Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
- 1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely ThunderCrypt Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
- 2) Use professional data recovery software
- – Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
- – Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
STEP VII: Preventive Security Measures
- 1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



