BeethoveN ransomware virus is created to encrypt valuable user data and extort victims for a ransom fee. All files that have the .BeethoveN file extension are affected and no longer workable. BeethoveN virus is based on the HiddenTear source code and copies its behavior. So the good news is that security researchers have managed to crack the code of HiddenTear ransomware and the freely available decryption tool may help victims to recover .BeethoveN files. But first, all BeethoveN malicious files should be removed from the infected PC.
Manual Removal Guide
Recover .BeethoveN Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Impacts of BeethoveN Ransomware Virus
BeethoveN virus is a data locker ransomware that utilizes strong encipher algorithm to modify the original code of predefined files so they cannot be accessed until a ransom fee is paid to criminals. They possess the unique decryption key that once employed is believed to decrypt all .BeethoveN files. Don’t rush to pay the ransom, the key may not be working or missing at all. Furthermore, there are alternative data recovery solutions.
Let’s reveal more details about the infection flow. It all begins with the execution of a malicious file called BeethoveN.exe dropped on the desktop folder. The file can start a sequence of malicious activities that infect the operating system and targeted data. First, it initiates a scan process of all drives to find files that belong to its predefined target data list. The list may include commonly used file types as they usually contain sensitive information. Thus documents, images, photos, archives, videos, music, text files are likely to be corrupted and renamed with the .BeethoveN extension during the ransomware virus infection.
Next, the ransomware may drop or create new files with particular functionalities that allow further malicious activities. Some malicious files modify Windows registry keys like Run and RunOnce enabling the execution of the ransomware each time the Windows is started. So during the manual removal process of BeethoveN ransomware virus, it is good to check for suspicious values in the following registry keys:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
At the end, BeethoveN crypto virus drops a ransom note to inform victims about the infection and provide further details how they are expected to act if they want to recover affected files.
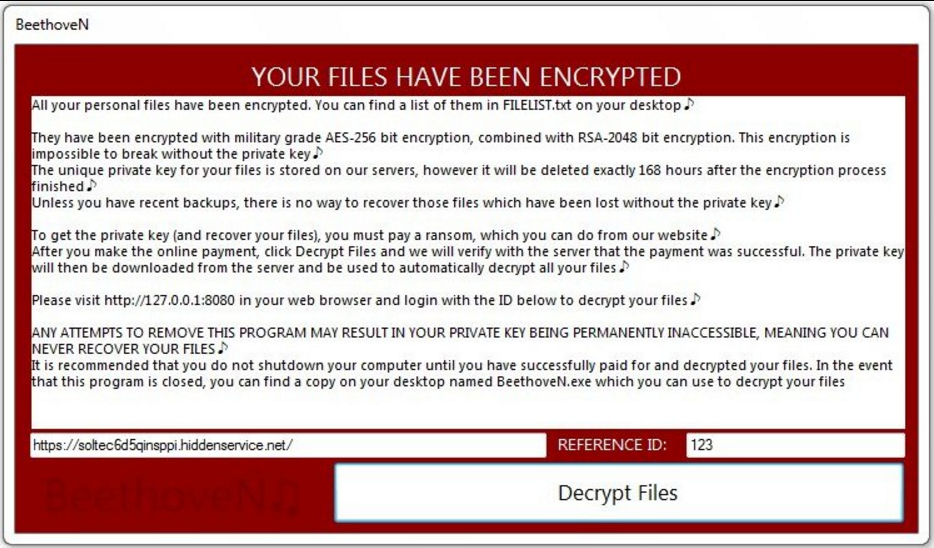
It seems that some ransomware developers have a classic taste of music. Even the ransom note of BeethoveN ransomware virus follows the set topic. Each sentence ends with a music note instead of a dot. However, the depicted information follows a traditional ransom note pattern that explains what has just happened, how to get the decryption key and regain encrypted files. It appears on the screen once the encryption is done. Victims see the following message:
YOUR FILES HAVE BEEN ENCRYPTED
All your personal files have been encrypted. You can find a list of them in FILEUST.txt on your desktop ♪
They have been encrypted with military grade AES-256 bit encryption, combined with RSA-2048 bit encryption. This encryption is impossible to break without the private key ♪
The unique private key for your files is stored on our servers, however it will be deleted exactly 168 hours after the encryption process finished ♪
Unless you have recent backups, there is no way to recover those files which have been lost without the private key ♪
To get the private key (and recover your files), you must pay a ransom, which you can do from our website ♪
After you make the online payment, click Decrypt Files and we will verify with the server that the payment was successful. The private key will then be downloaded from the server and be used to automatically decrypt all your files ♪
Please visit xxxx://127.0.0.1:8030 in your web browser and login with the ID below to decrypt your files ♪
ANY ATTEMPTS TO REMOVE THIS PROGRAM MAY RESULT IN YOUR PRIVATE KEY BEING PERMANENTLY INACCESSIBLE, MEANING YOU CAN NEVER RECOVER YOUR FILES ♪
It is recommended that you do not shutdown your computer until you have successfully paid for and decrypted your files. In the event that this program is closed, you can find a copy on your desktop named BeethoveN.exe which you can use to decrypt your files
[xxxxs://soltec6d5qinsppi.hiddenservice.net/] REFERENCE ID: 123
button [Decrypt Files]
What our team has noticed during our research is the witty humor of security researchers at MalwareHunterTeam. We have noticed a post on their Twitter account which presents BeethoveN ransomware virus with catchy text written in the BeethoveN spirit.
Hopefully, they will crack BeethoveN code soon, and all victims will be able to decrypt all .BeethoveN files.
Related: How to Remove MafiaWare Ransomware HiddenTear Based Virus
Distribution Techniques of BeethoveN Crypto Virus
BeethoveN virus payload is likely to be distributed via spam emails whose sender may pose as a legitimate source. The text, on the other hand, may be trying to convince you that the file attachment should be urgently opened. Beware of file PDF attachments that contain embedded word files as it is a standard distribution practice used by crooks. This technique allows them to obfuscate the malicious payloads of the threat in malicious macros embedded in the word document.
The threat itself may also be distributed through links that lead to compromised websites. Except in emails, such links may be presented in messages or posts on social media sites like Facebook and Twitter.
Remove BeethoveN Ransomware Virus and Restore Data
WARNING! Manual removal of BeethoveN ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
BeethoveN Ransomware Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .BeethoveN Files
WARNING! All files and objects associated with BeethoveN ransomware virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD BeethoveN Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
NOTICE: As BeethoveN ransomware is believed to be a HiddenTear variant, all of you who are victims of the threat can try to recover data with the freely available HiddenTear decryption tool developed by Avast specialists. You need to have at least one original copy of a .BeethoveN encrypted file which may help the decryption tool to get the decryption key. Afterward, the same key may be used for the rest .BeethoveN encrypted files. You can find more details how to use the decryption tool in the guide uploaded on No More Ransom website.
Download HiddenTear Ransomware Decrytor
In case that .BeethoveN files cannot be decrypted with the HidenTear decryptor, you can try the following alternative data recovery solutions.
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



