Karo virus is a ransomware that encrypts sensitive files and marks them with the .ipygh extension, read our removal guide to learn more.
Manual Removal Guide
Recover Karo Virus Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does Karo Virus Infiltrate the System?
Karo virus samples can be acquired with different methods. Depending on the attack campaign the criminals may utilize strategies that are best suited to the targets.
One of the detected ways of acquiring the Karo ransomware is by opening up infected email messages. They utilize social engineering tricks that confuse the targets into infecting themselves. This is usually done by sending the Karo virus binaries as file attachments or links in the body of the messages. Such emails feature templates that pose as legitimate companies or government institutions. The hackers use legitimate graphics and text to make the messages appear as being sent by the original source.
A large part of the Karo virus infections are done by sending infected payload documents and software installers. They utilize a medium in the form of a fake document. The criminals create files that may be of user interest such as invoices, letters and etc. that bundle the Karo virus code. Upon interaction with them malicious scripts are executed that deliver the malware. Usually this is done by using prompts that ask the victims to enable the built-in scripts (macros). If this is done the infection is triggered and the virus is downloaded from a hacker-controlled site and executed on the local machine. An advantage to using this method is the fact that some basic anti-virus applications cannot detect such behavior as malicious. The attack campaign that leads to the Kora virus infection relies on infected Microsoft Word documents with the doc or docx extensions. They load built-in PowerShell commands that lead to active infections.
Other infection strategies include the use of dangerous add-ons, especially popular with internet browsers. The so-called browser hijackers are a leading cause for spreading computer users. Upon infection they modify essential settings of the installed applications. The criminal developers aim to create compatible versions with the most popular software: Mozilla Firefox, Safari, Microsoft Edge, Internet Explorer and Google Chrome. Upon infection the following settings are changed to point to a hacker-controlled address: the default home page, new tabs page and search engine. These sites can be used to deliver the Karo virus or other threats. In addition they seriously endanger the privacy of the victims by harvesting sensitive information: cookies, browser history, bookmarks, settings, passwords, form data and account credentials.
Hackers can create their own download sites that may pose as legitimate sources of popular or freeware applications. They may use the same template system just like the email messages with the social engineering tricks. This tactic is used to confuse the targets into downloading files from them. P2P networks are very popular with hackers as well, especially BitTorrent trackers where pirate content is usually hosted.
Direct hacker attacks are also possible. The criminals attempt to use automated software that are able to infiltrate computers and networks if they use outdated applications. By always applying the latest updates to the installed software and operating system the users can protect themselves from such viruses.
The final versions of the Karo virus can also be delivered by botnet attacks and other related hacker means.
We recommend that everyone use a quality anti-spyware solution to rid themselves of the Karo virus. Once this is done a professional-grade data recovery application can be used to restore the affected files. See our detailed instructions below.
Related: EyLamo Virus, CryptoSpider Virus
Infection Flow of Karo Virus
The Karo virus is a newly discovered ransomware that appears to be made by an unknown hacker or criminal collective. During the initial security analysis its code did not display any correlation with any of the famous malware families. As a result the experts state that it is an independent creation made by an unknown hacker. At the moment the identity of the hacker or criminal collective behind it is not known.
After the infection has been made the Karo ransomware engine starts to execute its built-in set of actions. The virus contains several pre-execution checks that are mandatory – one of them involves stealth protection that prevent computer administrators and cyber security experts from discovering the infection. Such techniques involve anti-virtualization checks that prevent the malware execution in specific environments: virtual machines, debuggers and sandboxes. If the ransomware discovers that such an application is running it will automatically shut down and delete itself.
The next step is the gathering of sensitive system information. The Karo virus is able to extract data related to the hardware of the machines and their software configuration.
The Karo virus also hides the ransomware binary by using a code obfuscator – by using specific patterns the malicious code is hidden from analysis. Basic anti-virus and anti-spyware applications can miss such infections.
Before the encryption engine is started the Karo ransomware engine initiates a network server that is able to listen for incoming connections. This means that a module for C&C (command and control) servers may be present.
Once the checks have been made the encryption engine is started. It processes files based on a built-in list of target file type extensions. The captured samples so far indicate that the following extensions are being processes:
- txt – Plain text files.
- sql – A popular file format for databases.
- cs – Format for holding C# Source files.
- cpp – Format for holding C++ source code files.
- text – Used for holding office documents.
- js – JavaScript code and files.
- html – Web pages and documents.
- java – Used for holding different files related to the Java programming language.
- pl – Format for holding Perl source code files.
- c – Format for holding C source code files.
- mdb – Microsoft Access database files.
Based on the targets the file list used by the Karo virus may be modified. Once this process is complete a ransomware note is crafted in a “ReadMe.html” file. This is a rich text document that depicts a colorful background with the following text in a red overlay:
YOU HAVE BEEN INFECTED WITH RANSOMWARE, OPEN README FILE ON DESKTOP FOR DETAILS

The message serves as a warning for the victims of the Karo ransomware. They will find that a text document with hacker-provided recovery instructions has been created on their desktop. Depending on the configuration of the karo virus it may be based on several case scenarios:
- The hackers can opt to use social engineering tricks that blackmail the users into paying them a specified sum. Usually they are promised system and data recovery in exchange for a hefty sum. In most cases the payments are requested through anonymous digital currencies like Bitcoin. They are anonymous and cannot link the individual wallet holders to their owners from the transactions alone.
- The victims can get redirected via a link to a hacker-operated payment gateway where the requested sum may vary according to the quality and quantity of the encrypted data.
- The victims may be provided an email address or an instant messaging account that they have to contact to obtain the needed “decryptor”.
- A combination of the above methods.
All processed files are marked with the .ipygh extension. The cipher that was utilized in the process is the AES-256 military standard. The Karo virus is able to query all possible mounted volumes. This means that the ransomware engine is able to impact both mounted hard drives, removable storage and accessible network shares.
Some of the captured Karo virus showcase a ransomware message that reads the following:
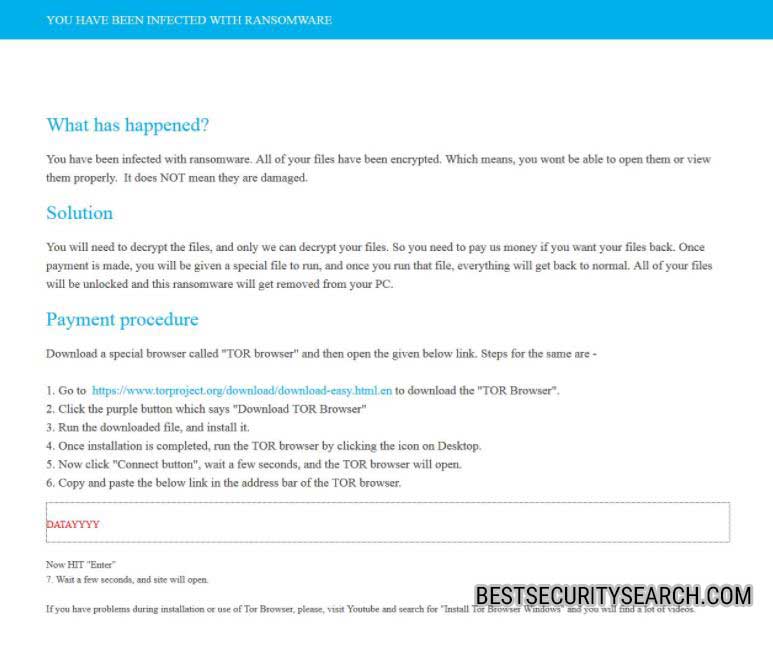
YOU HAVE BEEN INFECTED WITH RANSOMWARE
What has happened?
You have been infected with ransomware. All of your files have been encrypted. Which means, you wont be able to open them or view
them properly. It does NOT mean they are damaged.Solution
You will need to decrypt the files, and only we can decrypt your files. So you need to pay us money if you want your files back. Once
payment is made, you will be given a special file to run, and once you run that file, everything will get back to normal. All of your files
will be unlocked and this ransomware will get removed from your PC.Payment procedure
Download a special browser called “TOR browser” and then open the given below link. Steps for the same are-
1. Go to https://www.torproject.org/download/download-easy.html.en to download the “TOR Browser”.
2. Click the purple button which says “Download TOR Browser”
3. Run the downloaded file, and install it.
4. Once installation is completed, run the TOR browser by clicking the icon on Desktop.
5. Now click “Connect button”, wait a few seconds, and the TOR browser will open.
6. Copy and paste the below link in the address bar of the TOR browser.DATAYYYY
Now HIT “Enter”
7. Wait a few seconds, and site will open.If you have problems during installation or use of Tor Browser, please, visit Youtube and search for “Install Tor Browser Windows” and you will find a lot of videos.
From this we can conclude that the criminals have issued several versions of the malware. The ransomware note clearly does not specify an address of the TOR payment gateway – this gives out that the samples are early test versions that need to be updated to reflect the hacker’s resources and infrastructure.
It is possible that the Karo virus has been produced as a ransomware core. This allows hackers to trade its code on different hacker underground servers and trading platforms. As a result of this multiple variants of the Karo ransomware can be launched at the same against computer networks worldwide.
Karo virus is able to modify data found in the Windows operating system, including the deletion and modification of system files.
As this is an advanced ransomware strain we recommend that all users use a quality anti-spyware solution to recover
Remove Karo Virus and Restore Data
WARNING! Manual removal of Karo Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Karo Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover Karo Virus Files
WARNING! All files and objects associated with Karo Virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD Karo Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



